Know what your MCP Servers can do - before attackers exploit them
Enkrypt AI MCP Scanner discovers tools, analyzes capabilities and permissions, and surfaces high-risk exposure - so you can adopt MCP with clear ownership and least privilege.
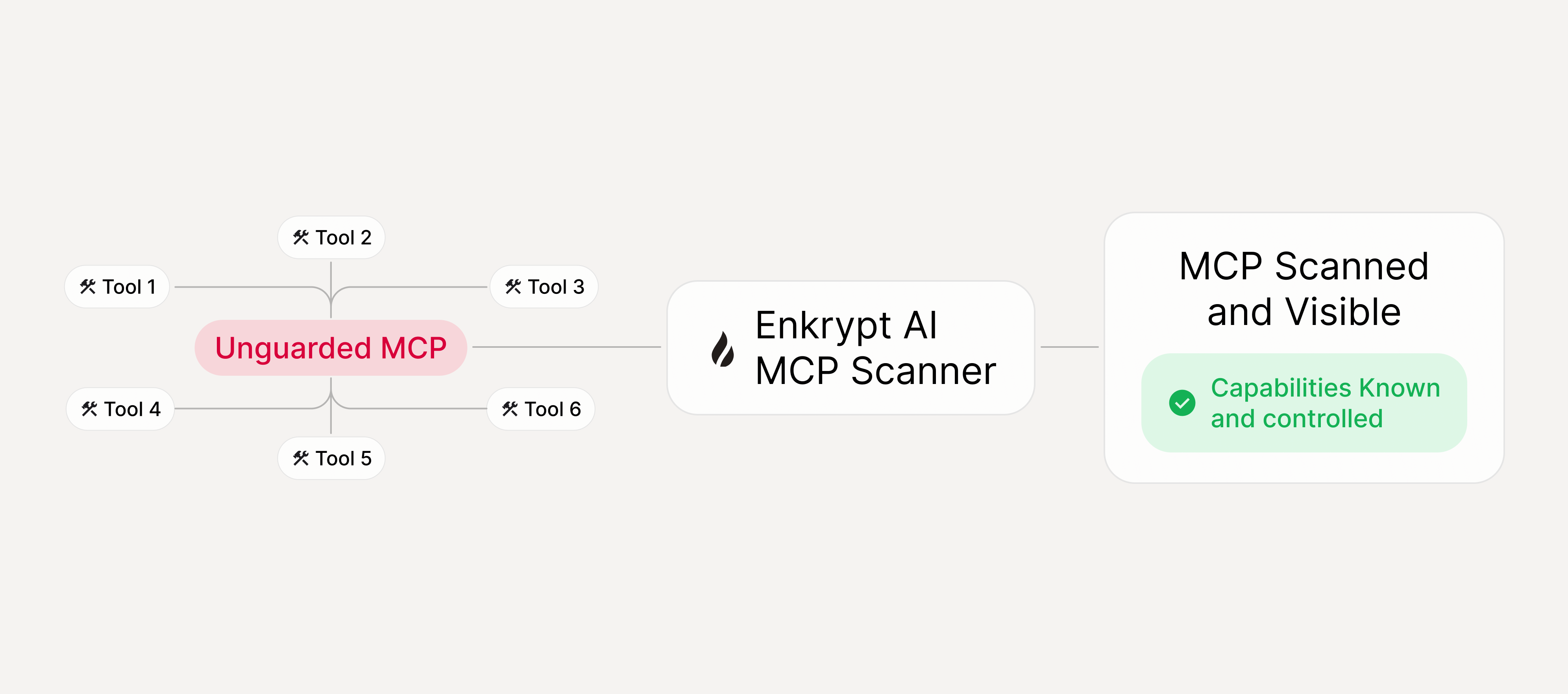
What MCP Scanner answers
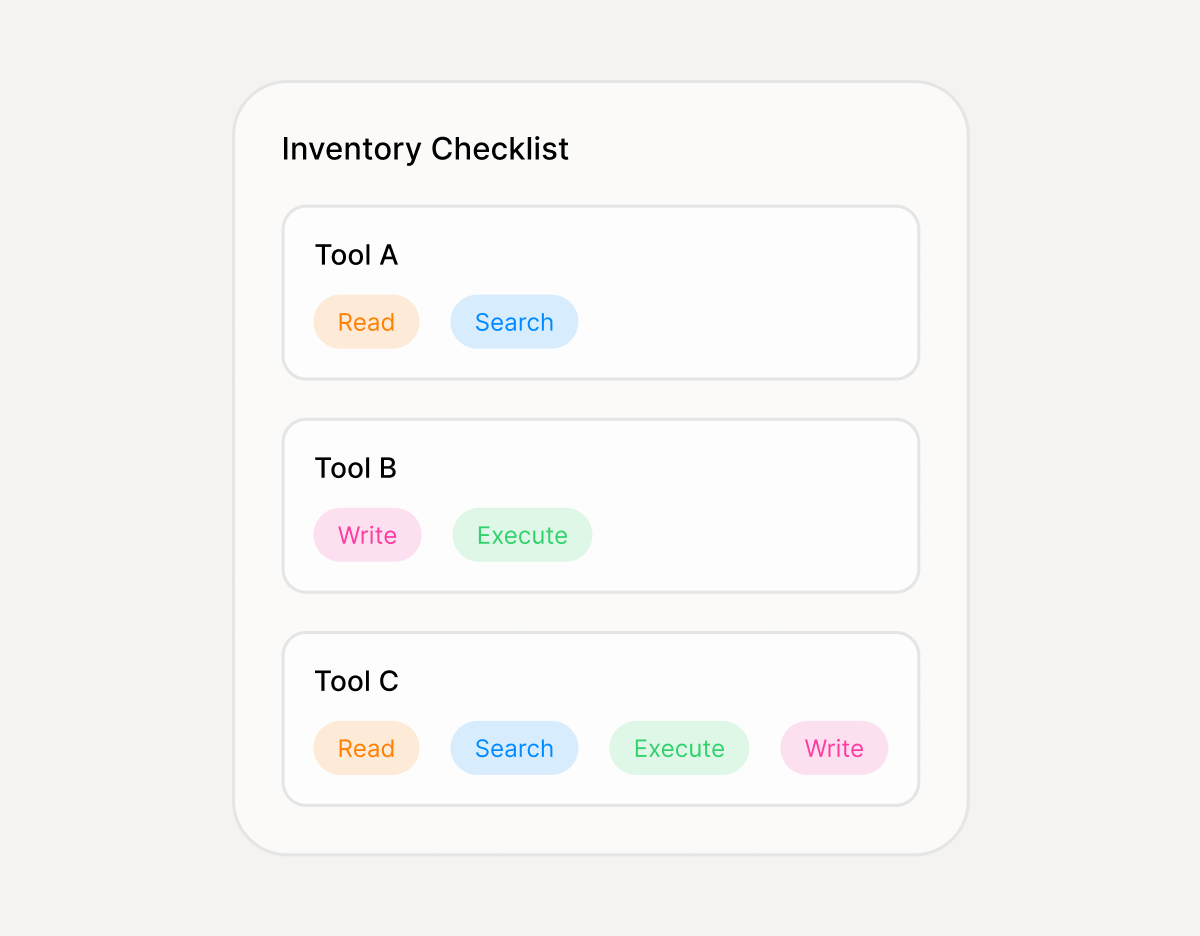
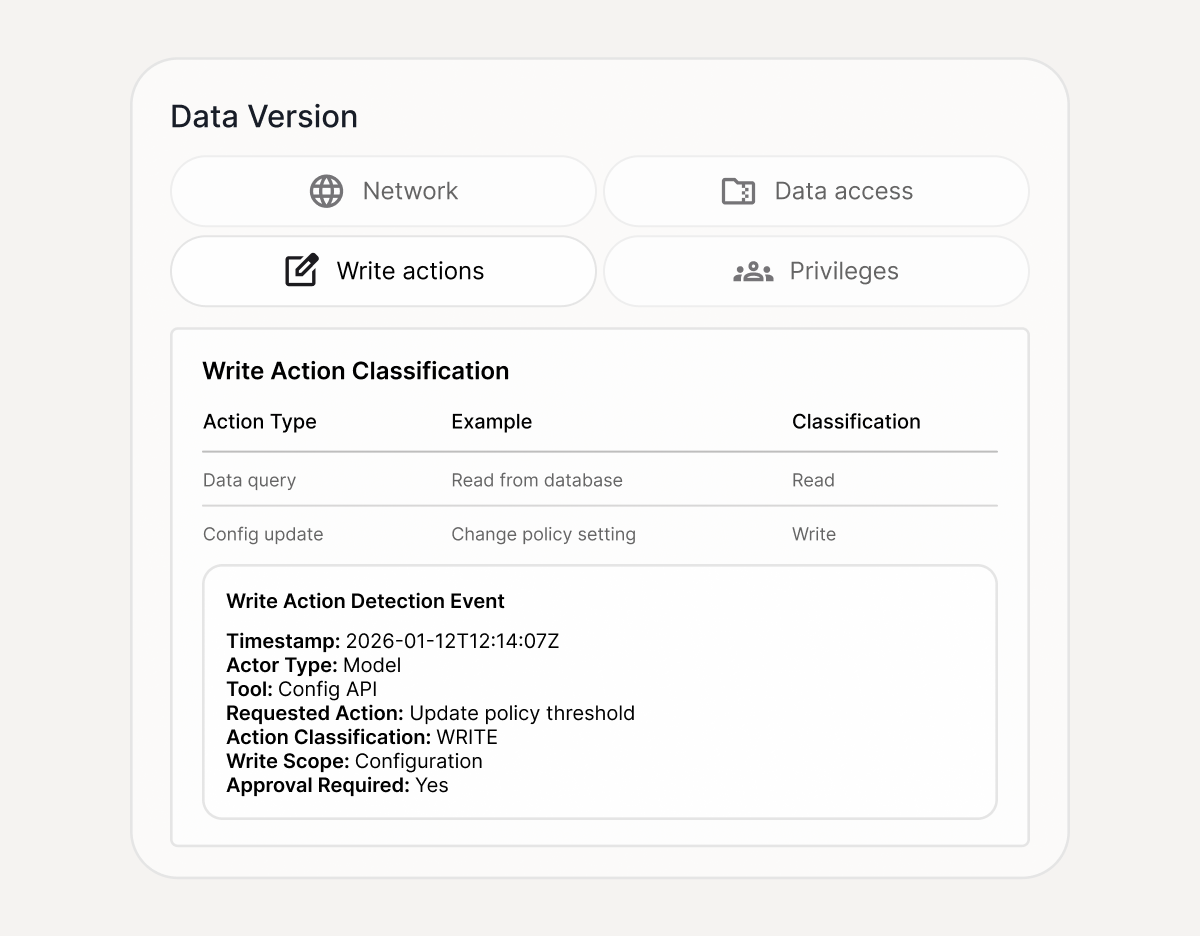
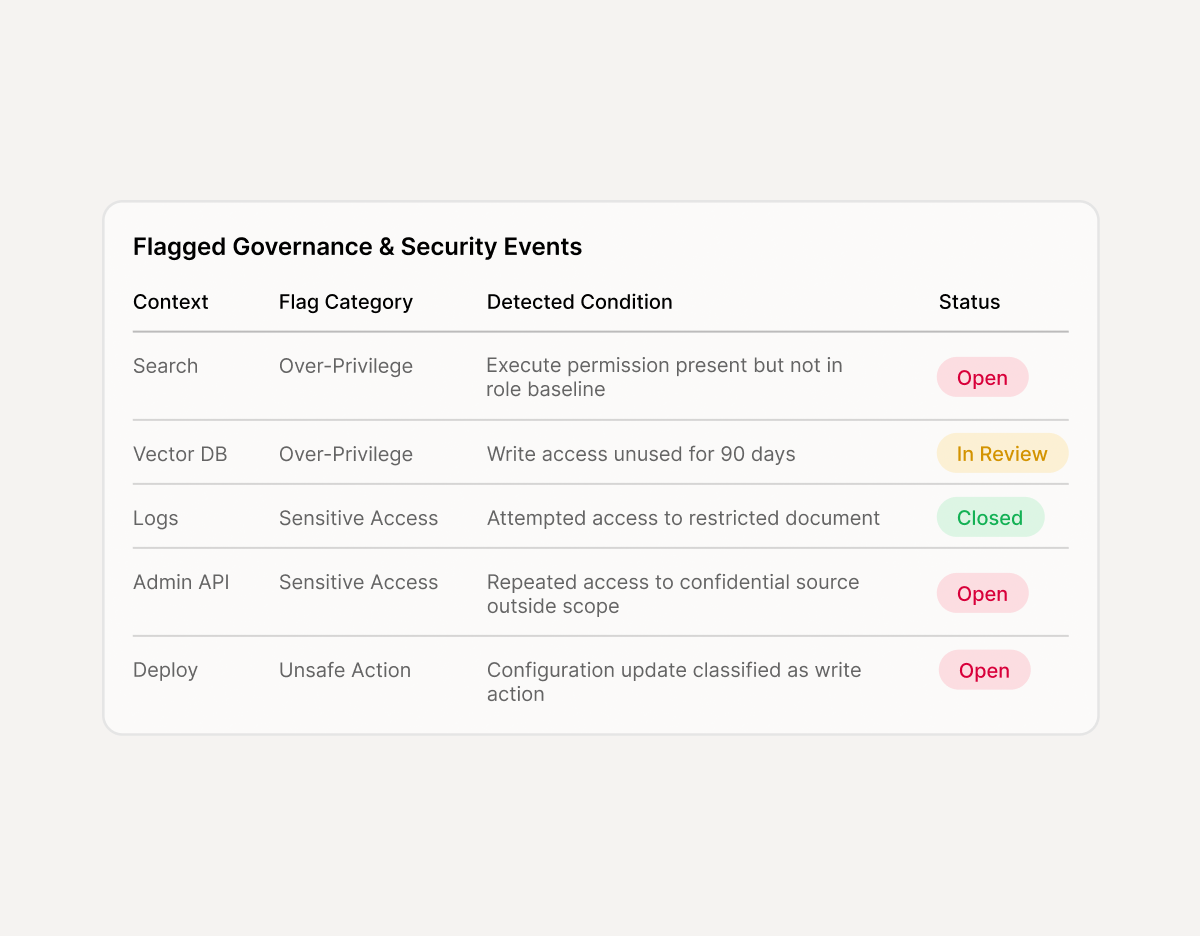
What you get
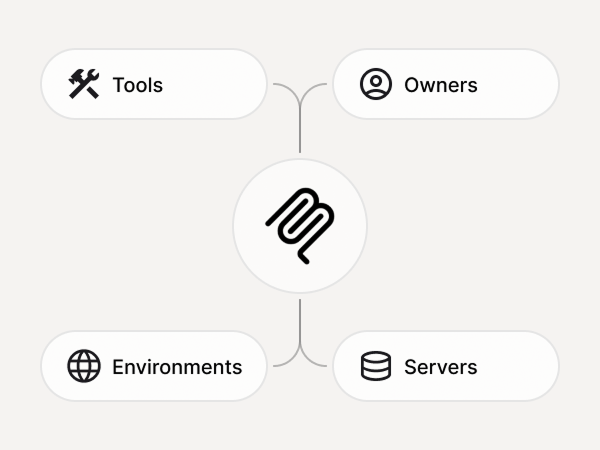
MCP Inventory
Servers, tools, capabilities, environments, owners
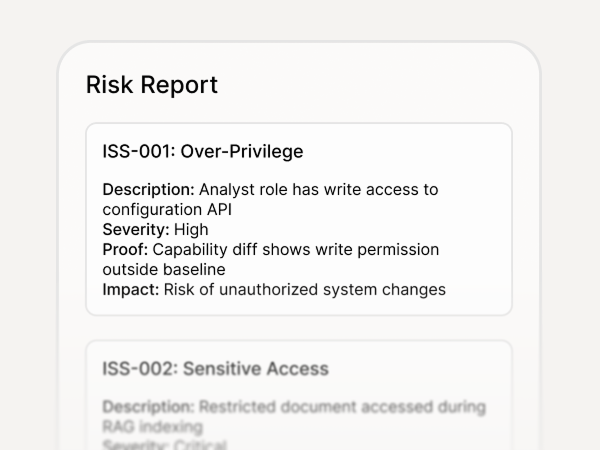
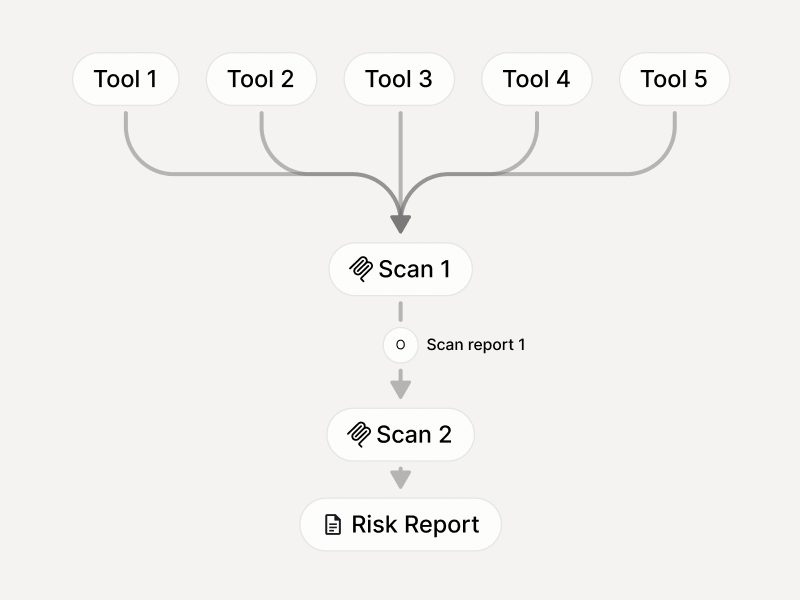
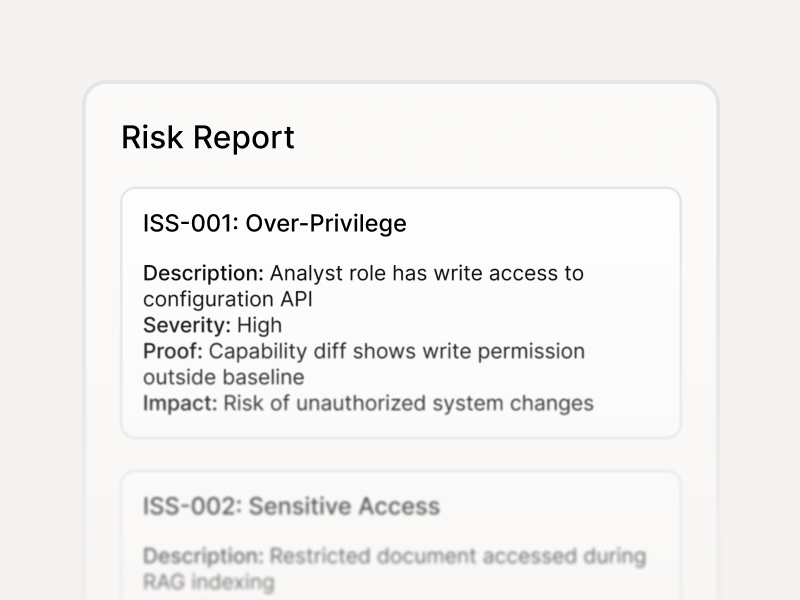
Risk Findings Report:
Prioritized issues with severity, proof, and impact
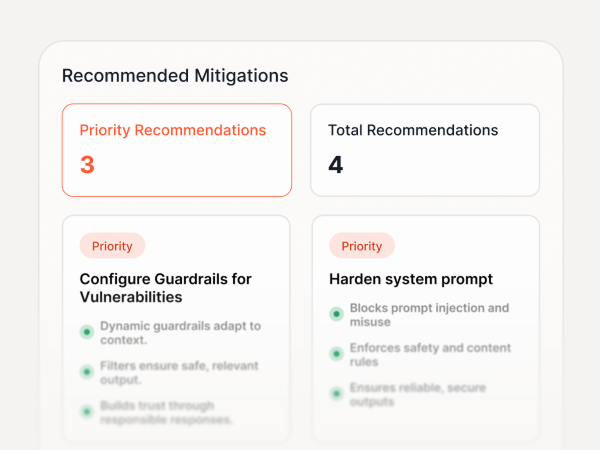
Remediation Plan
Least privilege changes, allowlists, and approval gates
Evidence
Exportable summaries for security and audit workflows

What MCP Scanner assesses
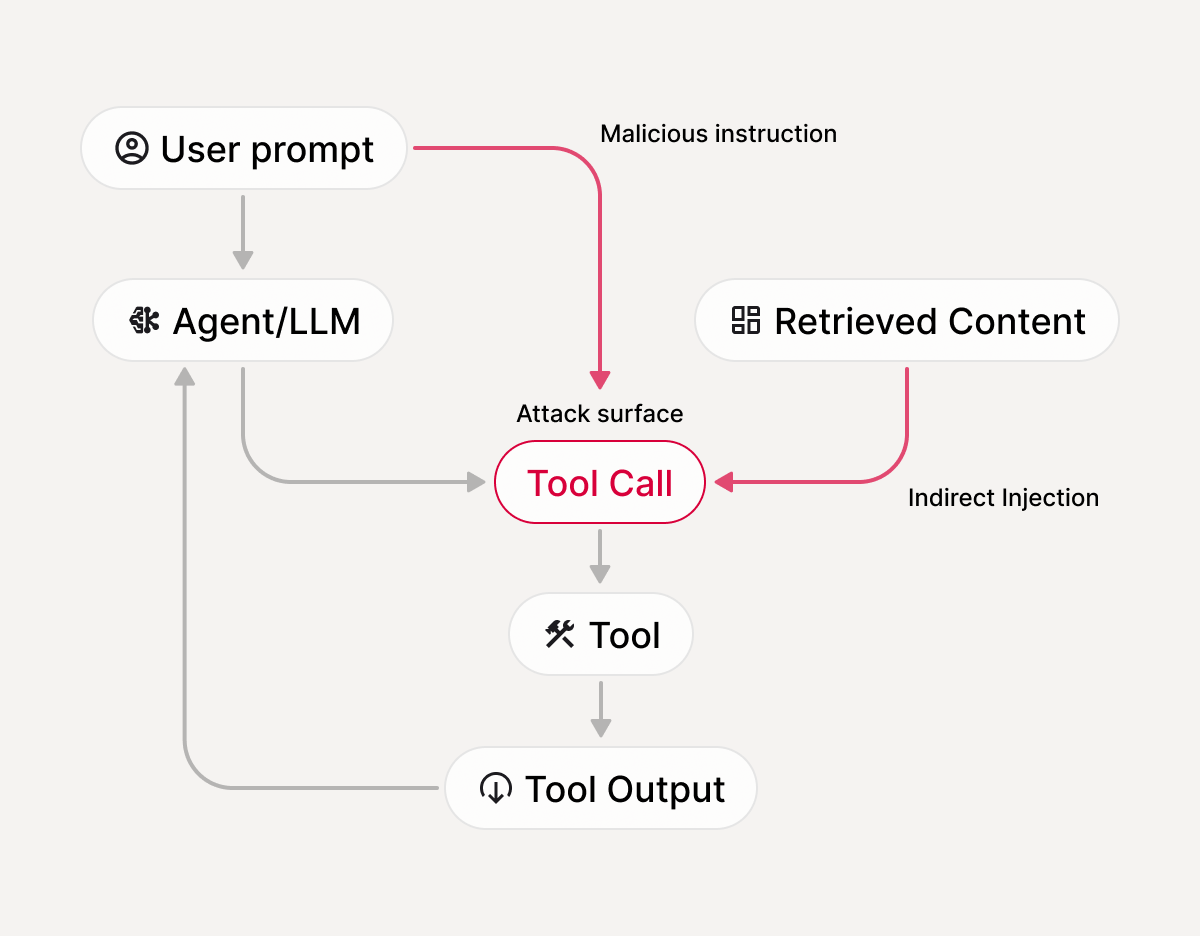
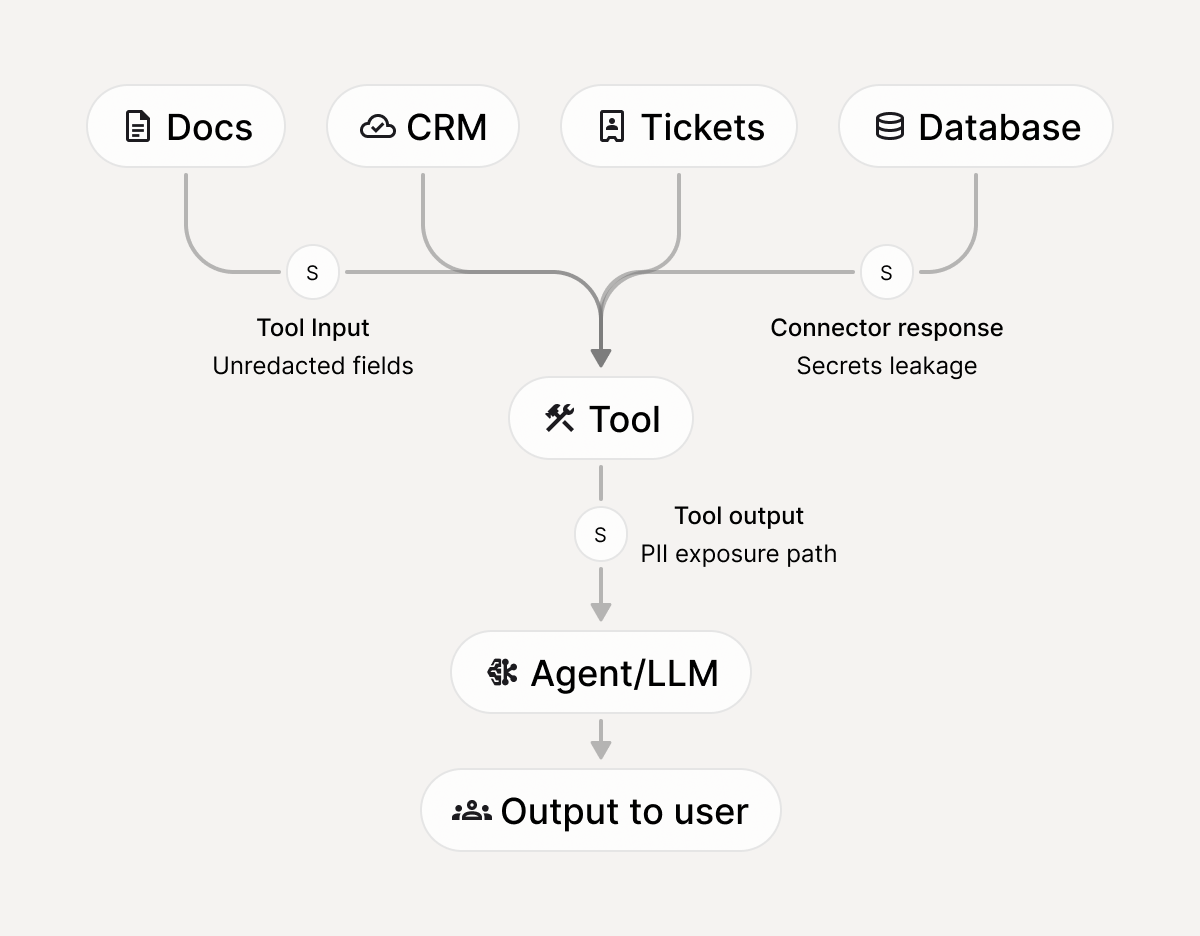
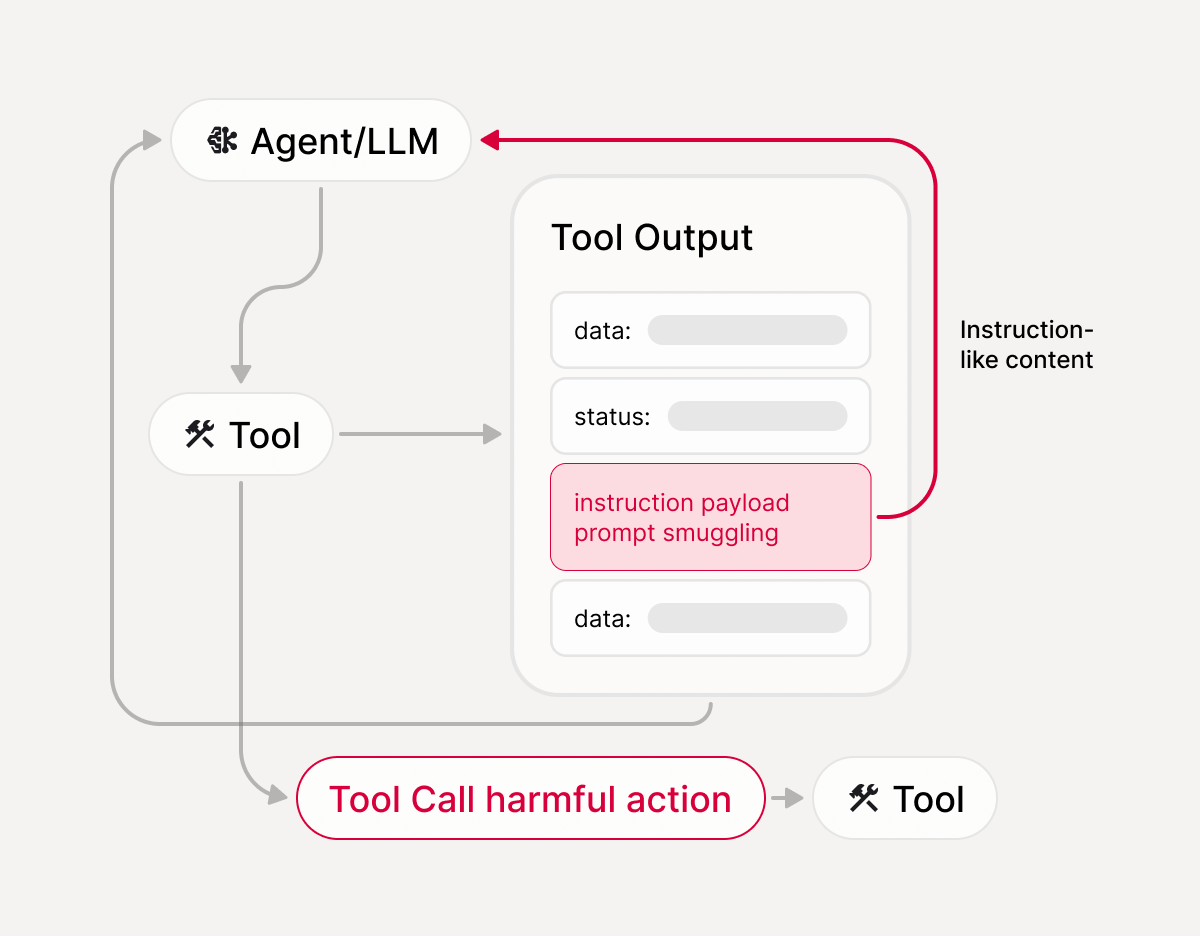
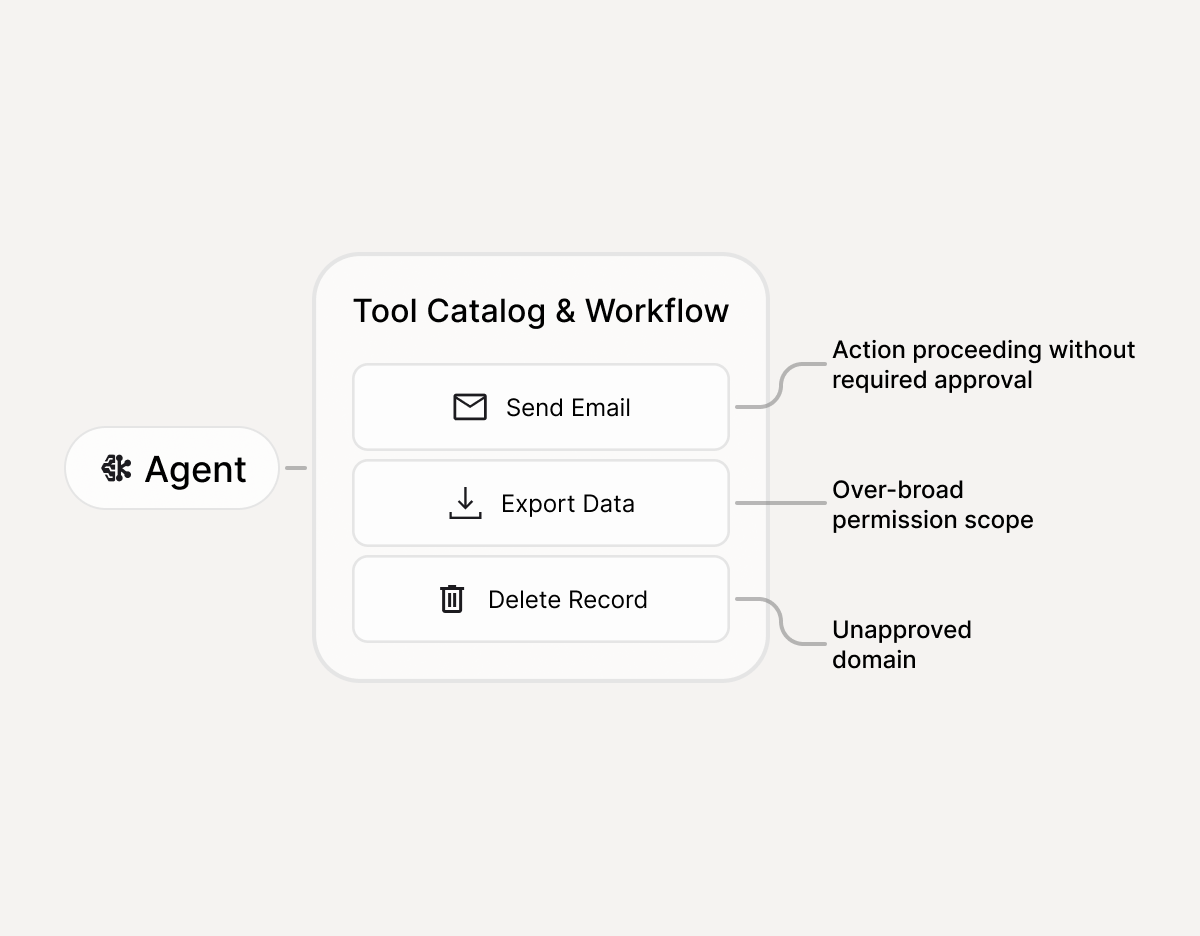
How it works
Submit your server
Automated scanning
Get detailed report
MCP Scan Request Successful
Email: -
URL : -
Result link also shared to your email,
results will be ready in 10 mins
results will be ready in 10 mins
Error :
Scan Your MCP Server for Free
Get a comprehensive security assessment in minutes
Result will be shortly in your inbox.
Thank you!
Oops! Something went wrong while submitting the form.
Built for production latency
Run scans:
Before go-live for new MCP servers/tools
Continuously to catch drift and shadow MCP
On-demand during reviews and incidents
Get Started
pip install enkryptai-sdk
from enkryptai_sdk import mcp_client
mcp_client.scan($MCP_REPO_LINK)

Complements MCP Gateway
Use MCP Scanner to discover and assess risk - then enforce policy in production with MCP Gateway.
Frequently Asked Questions
What does the MCP Scanner actually scan?
MCP servers and tool surfaces: configuration, permissions, tool schemas, endpoints, and common vulnerability patterns.
What are the concrete deliverables?
- Scan Report (PDF): top risks and prioritized remediation
- Findings Export (CSV/JSON): vulnerability, severity, reproduction notes, and fixes
- Approved/Denied Recommendations: what to allowlist vs block
Do you scan internal (private) MCP servers too?
Yes—scan internal MCP servers during development and before rollout, not just public MCPs.
How do you score severity?
Based on exploitability + impact (data access, action execution, permission scope), and exposure (public vs internal).
How is this different from the MCP Gateway?
Scanner finds vulnerabilities and risk before deployment. Gateway enforces policy at runtime and blocks unsafe tool execution.
Does this cover agentic supply-chain risk?
Yes—untrusted MCP servers/tools and poisoned tool catalogs are treated as supply-chain risk, with allowlist/denylist guidance.
How often should we scan?
Before launch, after tool updates, and on a recurring cadence for public tool ecosystems.

