Open-source control plane for MCP tool traffic
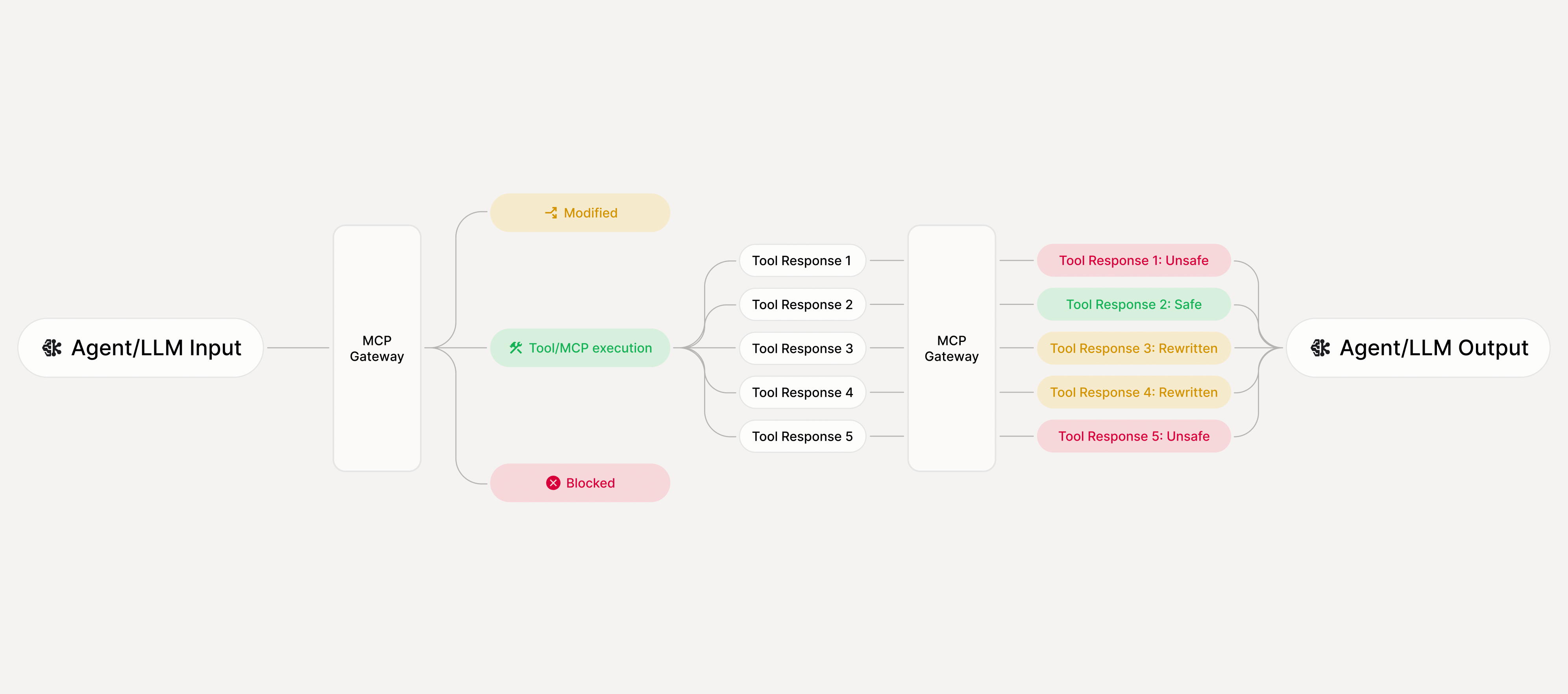
Enkrypt AI MCP Gateway is open source and sits inline between agents and MCP servers to approve, modify, or block tool calls - enforcing least privilege and producing an evidence trail you can audit.
What you get
Gateway deployment
An inline MCP proxy for requests and responses
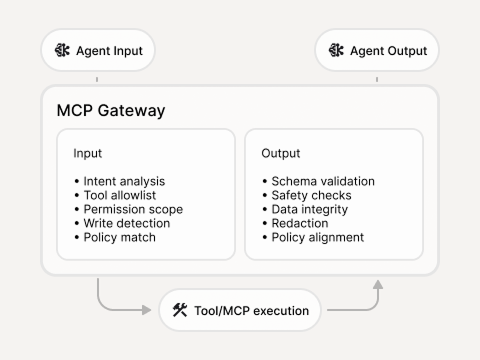
Policy decision log
Decision, reason, and policy/version applied
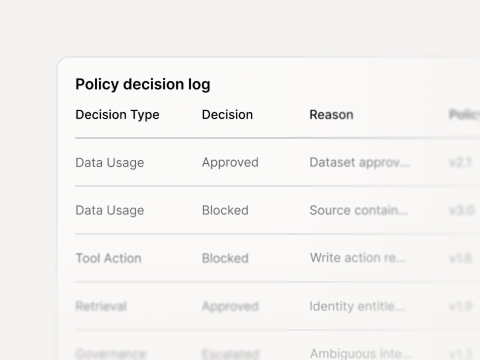
Action trace
Tool/server, actor, environment, time-stamps, outcomes
Approval receipts
Who approved what, when, and why
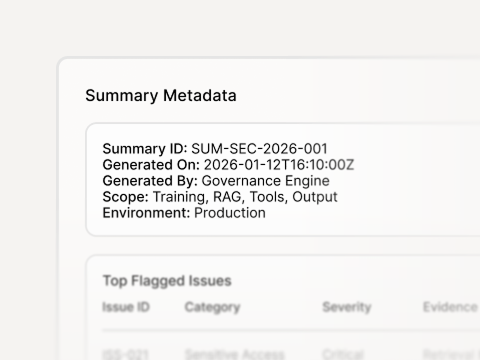
Evidence
Packages for reviews and governance workflows

Where MCP Gateway intercepts
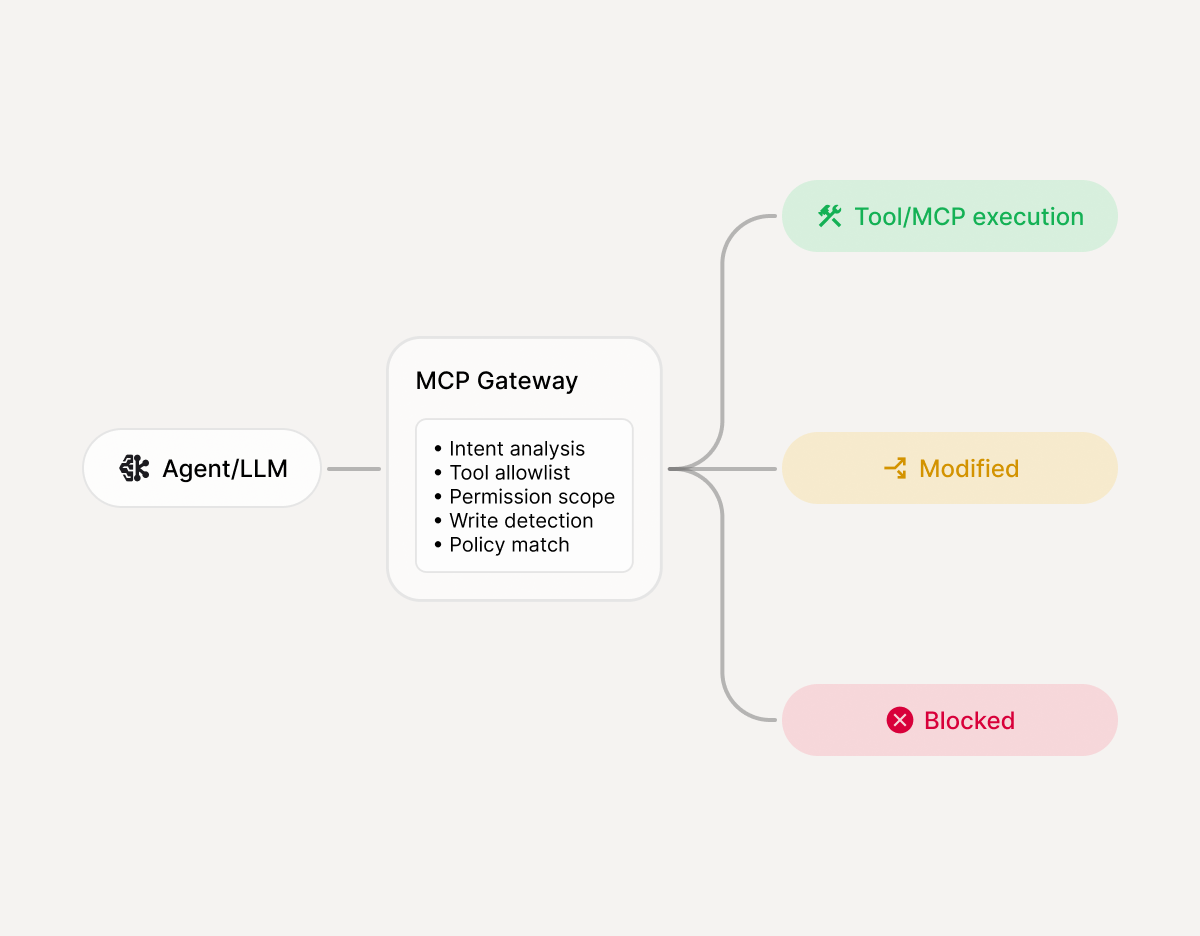
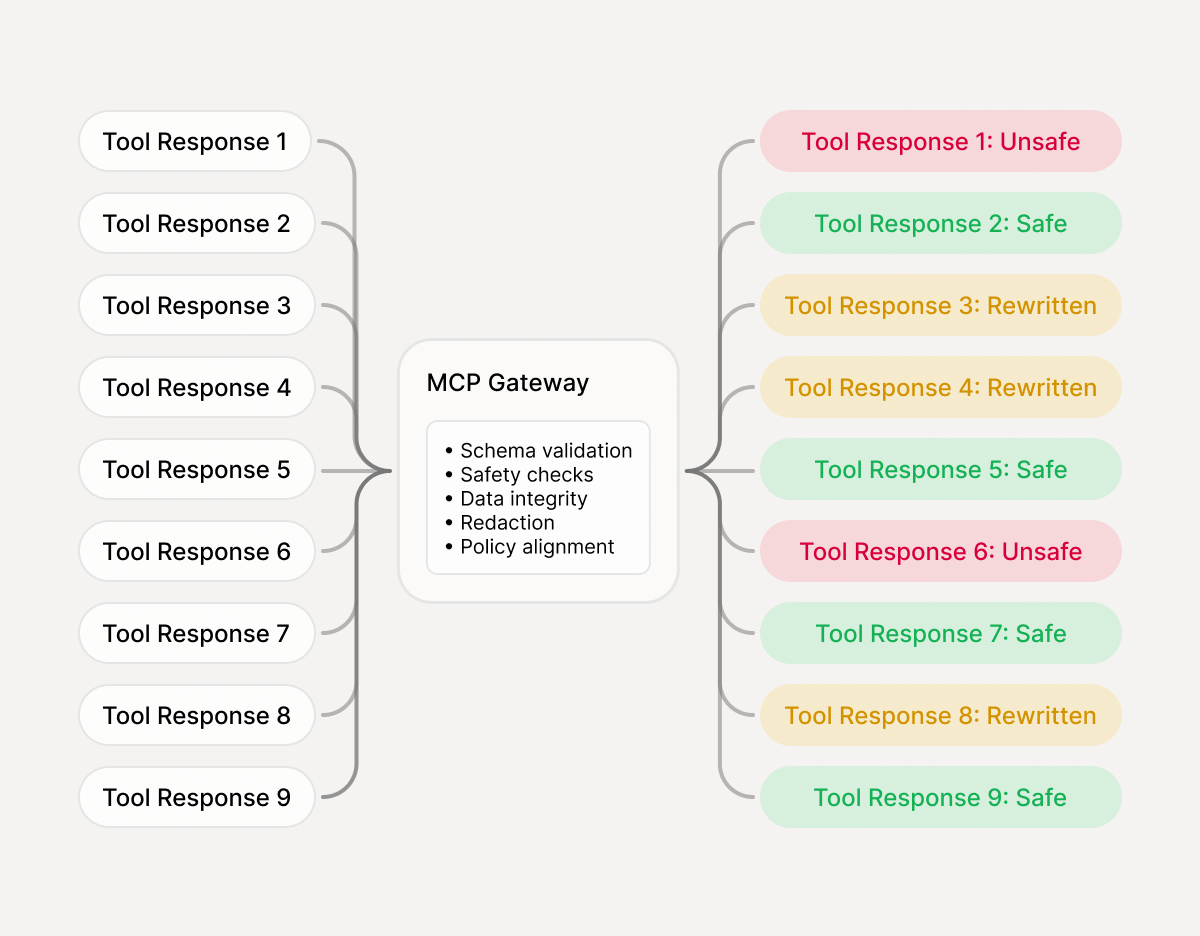
Enforcement modes
Open Source + Enterprise
Use the open-source gateway to deploy MCP controls quickly with full transparency.
Add Enkrypt when you need policy packs, audit-ready exports, and human experts for security reviews.


Guardrails, inline on MCP traffic
MCP Gateway doesn’t just route MCP calls—it runs Guardrails directly in the request/response path
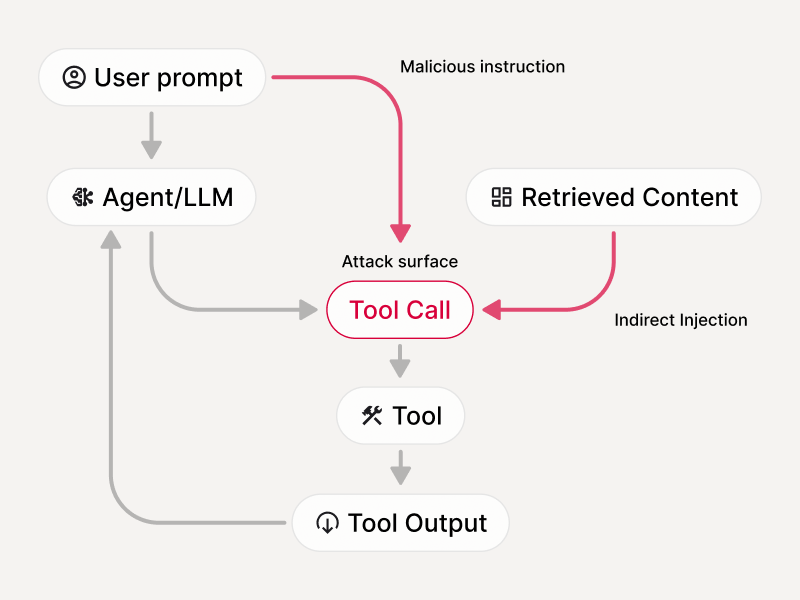
Detect injection-driven tool use before execution
- Prompt injection (direct + indirect) across text/audio/vision
- Tool misuse, privilege escalation, unsafe actions
- Data exfiltration, secrets leakage, connector abuse
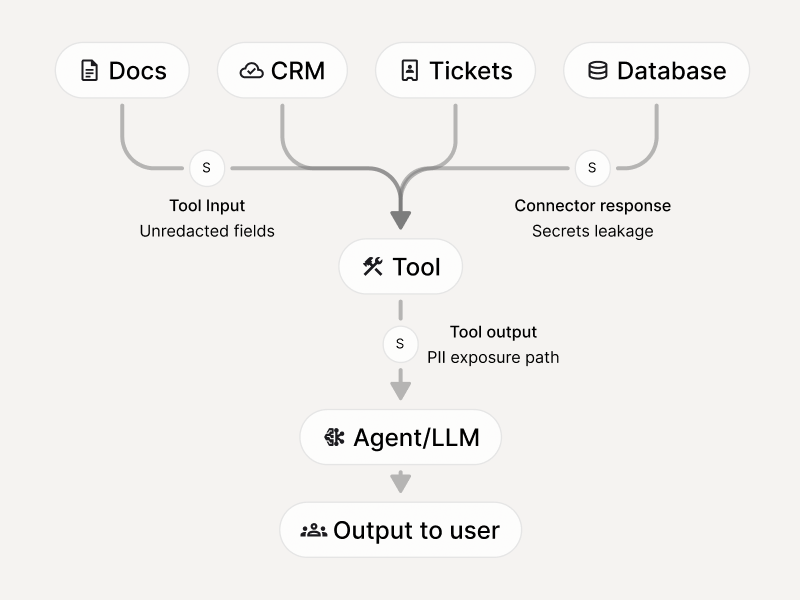
Prevent sensitive data leakage through tool inputs/outputs
- Jailbreaks and refusal bypass
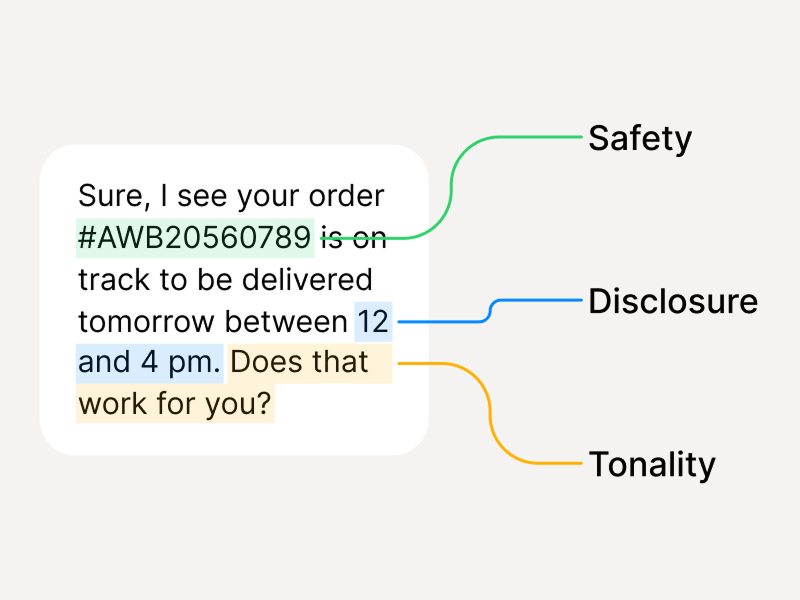
- Disallowed content, toxicity, brand-risk outputs
- Policy violations (tone, escalation, restricted topics)
Validate tool responses to stop response smuggling back into the agent loop
- PII/PHI/PCI handling failures
- Data minimization and retention violations
- Evidence generation for internal controls and audits
The risks it stops
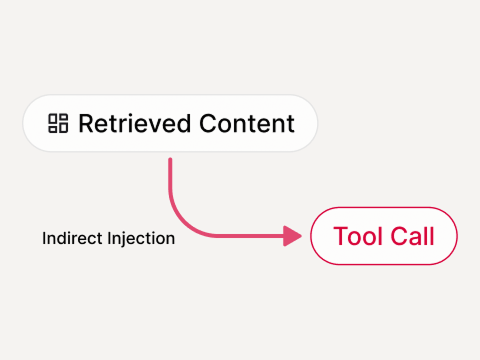
Injection-driven tool use
Malicious prompts steering actions
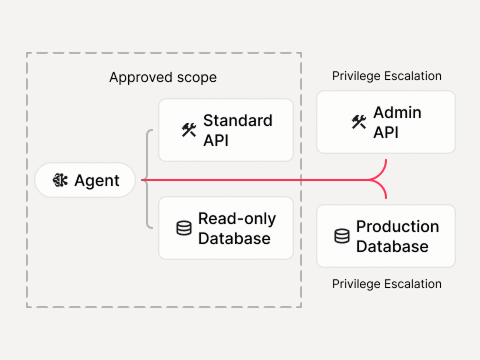
Privilege escalation
Agents calling tools outside intended scope
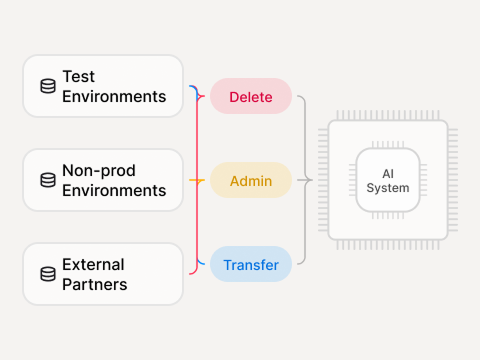
Exfiltration paths
Sensitive data leaking through tools/connectors
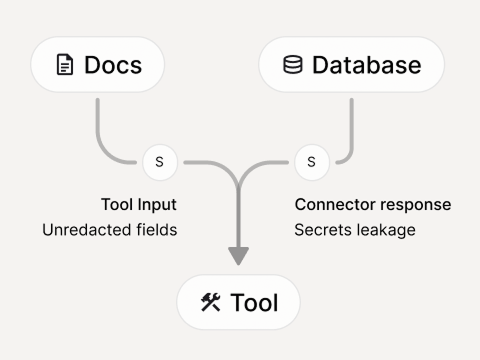
Response smuggling
Tool outputs injecting instructions back into the agent loop
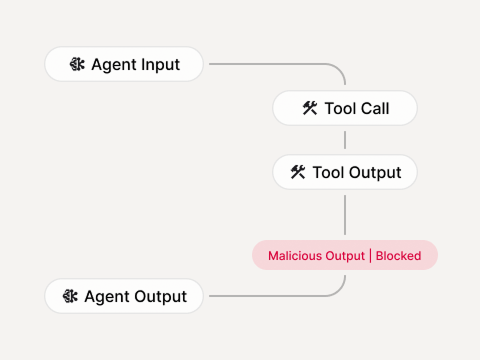
High-impact actions review
Delete/admin/transfer/network
Built for production latency
Designed for low-latency, high-throughput MCP traffic:
Inline decisions without breaking UX
Stable behavior under load
Fast enforcement
Deeper explanation when needed
Get Started
pip install enkrypt-sdk
pip install secure-mcp-gateway
secure-mcp-gateway generate-config
#Install on Cursor
secure-mcp-gateway install --client cursor
#Install on Claude
secure-mcp-gateway install --client claude-desktop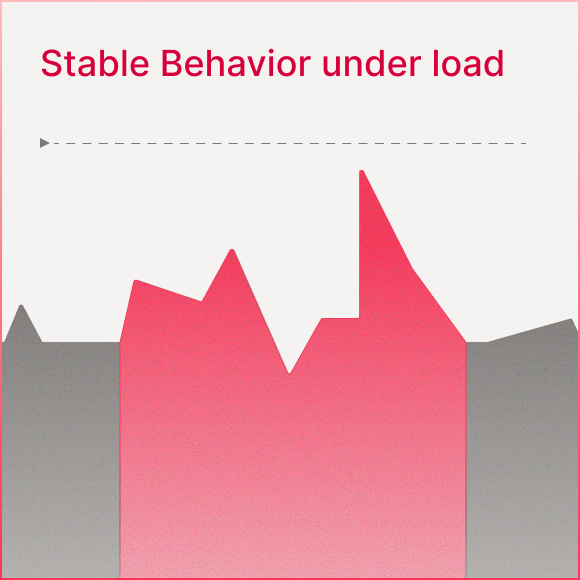

Works with MCP Scanner
Use MCP Scanner to discover and assess MCP risk - then enforce policy in production with MCP Gateway.

Frequently Asked Questions
What is the MCP Gateway?
A gateway layer for MCP tool traffic that lets you enforce policy and guardrails at the tool boundary—before actions execute.
Is the MCP Gateway open source? What’s the enterprise add-on?
The gateway is open source. Enkrypt AI adds enterprise capabilities like centralized policy management, tenant-aware enforcement, reporting, and support.
How does the Gateway work with Guardrails?
Guardrails policies can be enforced inline at the gateway: validate tool calls, constrain actions, and block unsafe execution pre-run.
How does the Gateway work with the MCP Scanner?
Scanner findings inform your approved registry and policy defaults; the Gateway enforces those decisions at runtime.
What are the concrete deliverables?
- Deployable gateway + configuration templates
- Approved tool registry patterns (allowlist/denylist)
- Policy-enforced decision logs for audits and incident response
Does this support multi-tenant enterprise SaaS?
Yes—policies can be scoped by tenant/role/environment so customers get the right isolation and controls.
Will this add latency?
Designed for production latency budgets with deterministic decisions and compact reason codes.
How do we deploy it?
Run as a sidecar/gateway in your tool path (Kubernetes, edge, or service mesh patterns), then expand coverage tool-by-tool.

