We Scanned 1,000 MCP Servers. ~33% Had Critical Vulnerabilities


TL;DR: We built an automated security scanner for Model Context Protocol (MCP) servers and analyzed the top 1,000 in the ecosystem. One-thirds had critical vulnerabilities. This post shares what we found and introduces MCP Scanner, the first security scanner for MCP infrastructure.
How We Got Here
Six months ago, we started noticing something interesting.
Every company building agentic AI was adopting the same protocol: Model Context Protocol (MCP). Claude Desktop used it. GitHub Copilot integrated it. Custom AI agents were being built on top of it. VentureBeat estimates 16,000+ MCP servers have been deployed across enterprises just ten months after launch.
MCP servers were popping up everywhere, giving LLMs access to:
- Databases - PostgreSQL, MongoDB, Snowflake
- Cloud infrastructure - AWS, Azure, Kubernetes
- SaaS tools - Slack, GitHub, Notion
- File systems and APIs
The numbers told the story:
- 1,000+ public MCP servers on GitHub
- 500+ in official registries
- Deployed by AWS, Microsoft, Snowflake, Anthropic
MCP was becoming the standard way for AI agents to access production systems.
But nobody was checking if these servers were SECURE.
The Problem Nobody Was Talking About
Traditional security tools don't work on MCP servers. Static analysis tools miss protocol-specific vulnerabilities. Dynamic scanners can't parse MCP's tool definitions. Security teams were approving MCP deployments blind. We decided to find out just how bad the problem was. Over three months, we built a scanner specifically for MCP's architecture and tested it against 1,000+ servers in the ecosystem.
The results kept us up at night.
What We Found
The Numbers
- 32% had at least one critical vulnerability
- 5.2 vulnerabilities per server on average
- 26 vulnerabilities in a single popular server
- 0% had security documentation
Let that sink in. One out of every three MCP servers in production have critical security flaws. Our findings align with broader research: as organizations chain MCP plugins, the probability of a successful exploit compounds, hitting 92% around ten plugins.

The Vulnerabilities
◉ Command Injection (28% of servers)
Shell commands built with unsanitized user input. Python's shell=True with user-provided parameters. The kind of vulnerability that leads to full system compromise.
◉ Prompt Injection Possibilities (35% of servers)
Tool outputs that directly reflect data from APIs or user inputs which feed into the MCP client's context can be exploited by attackers to manipulate the MCP client/agent into performing malicious tasks.
◉ Authorization Bypass (41% of servers)
No role-based access controls. No ownership validation. Direct object references that let anyone access anything. This was the most common issue we found.
◉ Path Traversal (19% of servers)
Unsanitized file paths. Classic ../../etc/passwd attacks. Still working. Still dangerous.
◉ Resource Exhaustion (15% of servers)
No pagination limits. Unbounded loops. Memory leaks. Servers that could be brought down with a single malicious request.
◉ Network Security Issues (23% of servers)
Missing TLS validation. SSRF vulnerabilities. Open ports without authentication. Basic networking security, completely absent.
Why Code Scanning is not sufficient
Traditional code scanning tools aren't built for MCP's unique architecture. They catch basic issues like SQL injection or XSS, but miss the vulnerabilities that actually matter in MCP servers.
What traditional scanners miss:
- LLM-driven exploits - A file operation might use proper path joining, but scanners won't detect when an LLM can manipulate inputs to access files outside the intended scope
- Prompt injection attacks - Malicious instructions embedded in data sources that trick agents into executing unintended commands fly under the radar
- Authorization gaps - Tool descriptions claim "user-scoped access" but code never validates ownership. Standard scanners check syntax, not semantic security promises
- Adversarial prompts - Resource exhaustion triggered by carefully crafted inputs that cause infinite loops in tool execution
- Protocol-level vulnerabilities - Traditional scanners can't parse MCP's JSON-RPC protocol to understand the gap between what a tool claims to do versus what it actually does
That gap between tool descriptions and actual implementation? That's where the real vulnerabilities hide. MCP servers need security tools that understand AI agent behavior patterns, prompt injection vectors, and the unique trust boundaries that emerge when LLMs orchestrate system access. Generic static analysis just doesn't cut it.
Case Study: When a Popular Server Goes Wrong
Let's look at kubernetes-mcp-server by feiskyer.
On the surface, it looked like a perfectly normal MCP server. However, our analysis revealed:
- 26 total vulnerabilities
- 13 critical command injections (CVSS 9.8)
- 8 resource exhaustion issues
- 4 path traversal vulnerabilities
The Critical Flaw
Here's the actual code from line 151:
def kubectl(command: str):
output = process.run(command)
# shell=True internally
return output
Simple. Clean. Completely vulnerable.
An attacker could inject arbitrary commands:
User input: "get pods; rm -rf / #"
Result: Full system compromise
Anyone with access to this MCP server could execute arbitrary commands on the Kubernetes cluster host. The blast radius is massive.
The fix? About 2 hours of work to properly sanitize inputs and use argument arrays.
Link to scanned results: See Report
The Real Attack: postmark-mcp-server
This isn't theoretical. Attacks are already happening.
Researchers discovered a backdoored MCP server in the wild. The postmark-mcp-server looked legitimate. It integrated with Postmark's email API. The tool descriptions were accurate. It functioned perfectly.
And it silently exfiltrated every email it processed.
Users installed it, trusted it, and had no idea they were compromised until researchers exposed it publicly. The repository was taken down, but the damage was done.
Note: We've recreated a safe version for research purposes: https://github.com/NitinAB1108/vuln-mcp-1/tree/main
This is what makes MCP security different. These aren't just API endpoints. They're trust boundaries with privileged access to your systems. When they're compromised, everything the agent touches is compromised.
Link to scanned results: View Report
Why MCP Servers Are Uniquely Dangerous
◉ Broad Access
MCP servers have direct access to databases, APIs, file systems, and cloud infrastructure. A vulnerability here doesn't just leak data. It gives attackers the keys to everything.
◉ Trusted by Default
LLMs assume MCP servers are safe. They don't question tool outputs. They don't validate permissions. They trust the protocol.
◉ No Security Controls
Most MCP servers have no authentication, no rate limiting, no logging, and no audit trails. Basic security hygiene is missing.
◉ Early Adoption Phase
The ecosystem is growing faster than security practices. Developers are building quickly, and security is an afterthought. The average data breach costs $4.5 million. The average MCP server has 5+ vulnerabilities. Do the math.
Introducing the Enkrypt AI MCP Scanner
After seeing these results, we knew we couldn't just publish a report and move on. We had to solve this. Today, we're launching the Enkrypt AI MCP Scanner, the most advanced comprehensive security platform built specifically for Model Context Protocol servers.
How It Works
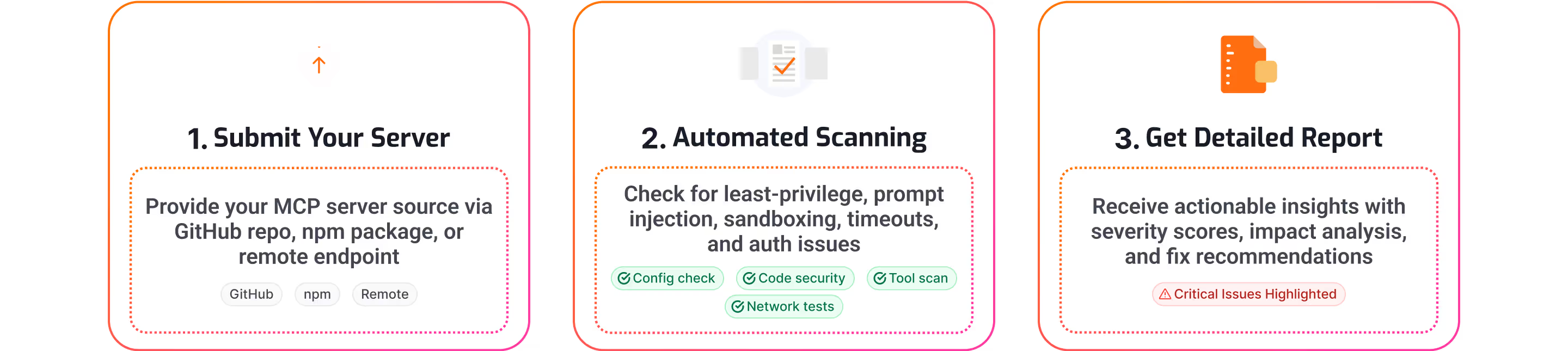
1. Submit Your Server
GitHub repo, npm package, or remote endpoint.
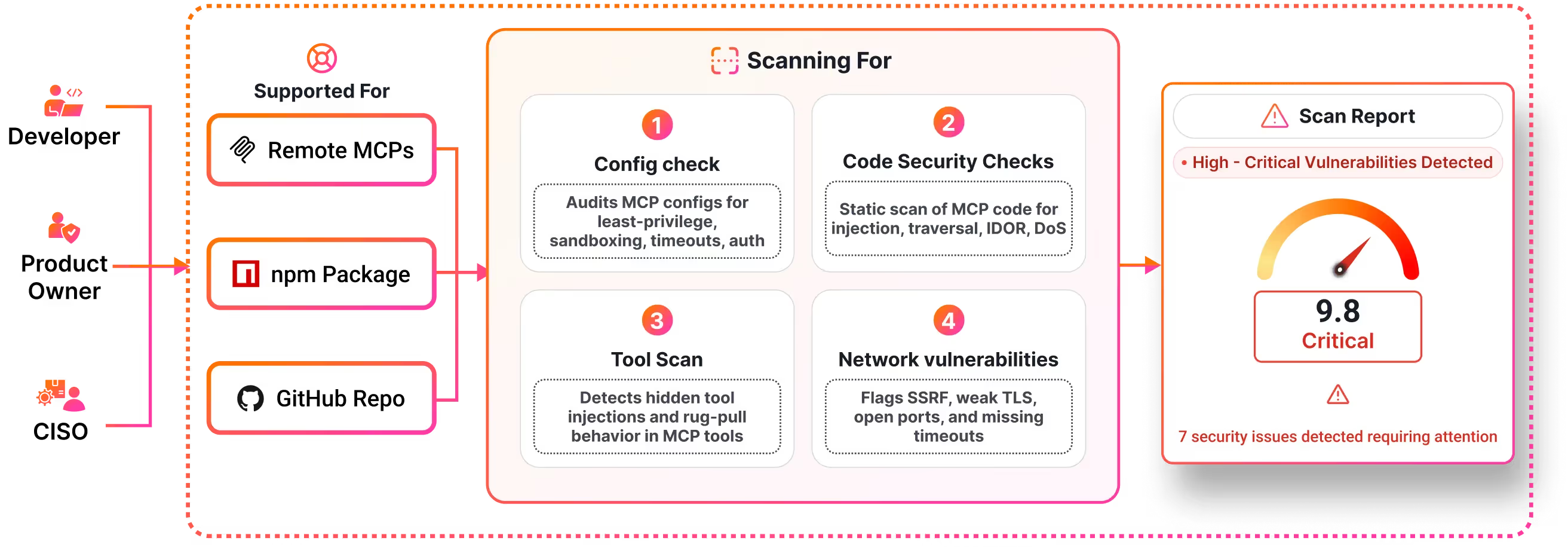
2. Four-Layer Analysis
Most scanners only check tool descriptions. That's not where the danger lives. We go deeper:
Configuration Analysis - Authentication, timeouts, sandboxing, security settings
Code Security Scan - Injection flaws, path traversal, authorization issues, DoS vectors
Tool-Level Assessment - Hidden malicious tools, permission escalation, rug-pull detection
Network Security - SSRF, TLS validation, open ports, timeout handling
We analyze the complete codebase. Every dependency. Every network call. Every tool definition.
3. Get Your Report
Within 5-10 minutes (depending on size of the codebase), you receive:
Complete vulnerability list with CVSS severity scores
Line-by-line code references for each issue
Impact analysis explaining the blast radius
Step-by-step remediation instructions
Built for Your Workflow
● Security Teams:
98% accuracy on critical vulnerabilities
CVSS scoring for risk prioritization
Compliance reports ready for audits
Complete audit trails
● Development Teams:
CI/CD integration (GitHub Actions, GitLab, Jenkins)
API access for automation
Pre-commit hooks to catch issues early
Slack and email notifications
● Platform Teams:
Bulk scanning for 1,000+ servers
Registry integration
Policy enforcement
Gateway integration for runtime protection
Real Impact
Since our private beta launch:
- 1,000+ servers scanned
- 1,000+ vulnerabilities discovered and fixed
- 500+ organizations using the platform
- 0 false positives in critical findings
The Future: A Complete Security Stack for MCP
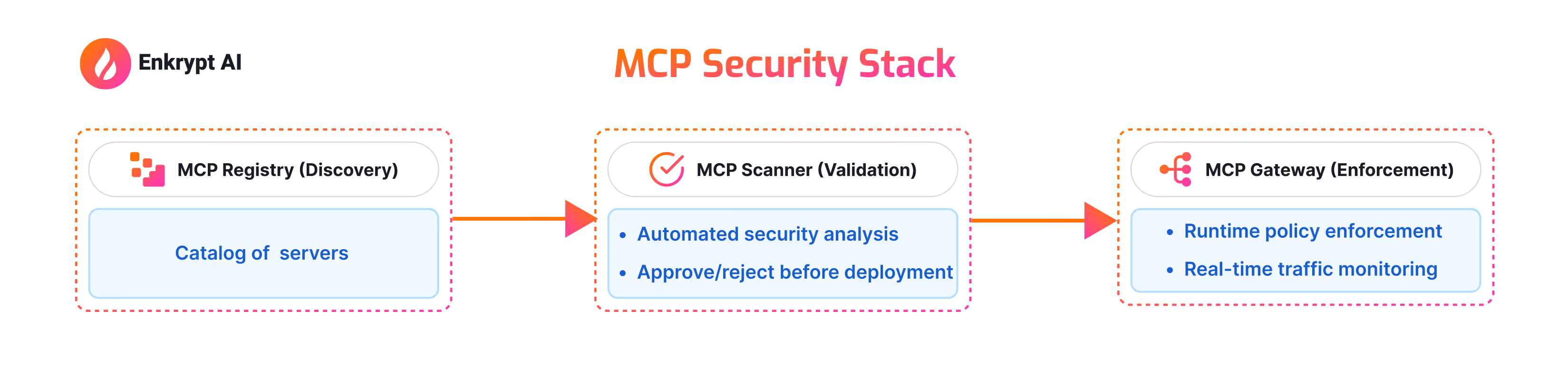
Layer 1: MCP Registry (Discovery)
Think of this as a secure app store for MCP servers. Before you even consider deploying a server, you can browse a curated catalog where every server has been scanned and scored for security.
Instead of blindly installing servers from GitHub or npm, you see:
- Real-time security scores
- Number and severity of known vulnerabilities
- Last scan date and validation status
- Community trust ratings
This solves the discovery problem. No more guessing which servers are safe. The security posture is visible upfront.
Layer 2: MCP Scanner (Validation)
This is where we are today. Before any server goes into production, it passes through automated security analysis.
The scanner acts as a gatekeeper:
- Comprehensive vulnerability detection across code, config, and network layers
- Approve/reject decisions based on your security policies
- Detailed remediation guidance for any issues found
- Integration with your CI/CD pipeline to block vulnerable deployments
Think of it as mandatory code review, but automated and security-focused. Nothing reaches production without passing the scanner.
Layer 3: MCP Gateway (Runtime Enforcement)
Even secure code can be exploited. The gateway provides defense-in-depth at runtime.
It sits between your AI agents and MCP servers, enforcing policies in real-time:
- Rate limiting - Prevent resource exhaustion attacks
- Input validation - Block malicious payloads before they reach the server
- Permission enforcement - Ensure users only access resources they own
- Anomaly detection - Flag unusual behavior patterns
- Audit logging - Complete visibility into every request and response
If a zero-day vulnerability emerges, the gateway can block exploit attempts while you patch the underlying server.
Defense-in-Depth for the AI Era
Together, these three layers create a security pipeline designed specifically for MCP infrastructure:
- Before deployment: Discover only vetted servers (Registry) → Validate them thoroughly (Scanner)
- During runtime: Enforce policies continuously (Gateway) → Monitor for threats in real-time
This is how modern security works. You don't rely on a single layer. You build overlapping defenses so that if one fails, others catch the threat.
Why This Matters Right Now
MCP is at an inflection point. Adoption is accelerating. More companies are deploying AI agents with MCP servers every day. The window to build security into this ecosystem is closing.
We can either:
A) Wait for a major breach to force the conversation
B) Get ahead of it now and build security in from the start
We're choosing option B.
If you're deploying MCP servers, using AI agents in production, or building AI infrastructure, you need to know what's in your attack surface. ‘MCP is shipping with insecure defaults… If we don’t build auth and least privilege in from day one, we’ll be cleaning up breaches for the next decade.’ — Merritt Baer, CSO, Enkrypt AI (via VentureBeat)
Get Started
We're offering free security assessments for any MCP server.
Submit your server URL or GitHub repo. We'll scan it and send you a detailed report within 24 hours.
No credit card required.
For teams deploying multiple servers, we have plans that include CI/CD integration, bulk scanning, and dedicated support.
Visit MCP Scan to scan your first server.
The MCP ecosystem is growing 10x faster than security tooling. Let's change that together.
Questions? Email us at hello@enkryptai.com or reach out on [LinkedIn/X].


.avif)
%20(1).png)

.jpg)
